Rilasciato Asterisk 13.11.2
Il giorno 09 settembre 2016, il Team di Sviluppo di Asterisk ha annunciato il rilascio di Asterisk Asterisk 13.11.2.
Dal post originale:
The release of Asterisk 13.11.2 resolves an issue reported by the community and would have not been possible without your participation.
Thank you!
The following is the issue resolved in this release:
Bugs fixed in this release:
-----------------------------------
* ASTERISK-26349 - 13.11.1 res_pjsip/pjsip_distributor.c: Request 'REGISTER' failed (Reported by Dmitry Melekhov)
For a full list of changes in this release, please see the ChangeLog:
http://downloads.asterisk.org/pub/telephony/asterisk/ChangeLog-13.11.2
AST-2016-007: RTP Resource Exhaustion
Il giorno 08 settembre 2016, l'Asterisk Security Team ha rilasciato il seguente post.
Dal post originale:
Asterisk Project Security Advisory - AST-2016-007Product Asterisk
Summary RTP Resource Exhaustion
Nature of Advisory Denial of Service
Susceptibility Remote Authenticated Sessions
Severity Moderate
Exploits Known No
Reported On August 5, 2016
Reported By Etienne Lessard
Posted On
Last Updated On September 8, 2016
Advisory Contact Joshua Colp <jcolp AT digium DOT com>
CVE NameDescription The overlap dialing feature in chan_sip allows chan_sip to
report to a device that the number that has been dialed is
incomplete and more digits are required. If this
functionality is used with a device that has performed
username/password authentication RTP resources are leaked.
This occurs because the code fails to release the old RTP
resources before allocating new ones in this scenario. If
all resources are used then RTP port exhaustion will occur
and no RTP sessions are able to be set up.Resolution If overlap dialing support is not needed the “allowoverlapâ€
option can be set to no. This will stop any usage of the
scenario which causes the resource exhaustion.If overlap dialing support is needed a change has been made
so that existing RTP resources are destroyed in this
scenario before allocating new resources.Affected Versions
Product Release
Series
Asterisk Open Source 11.x All Versions
Asterisk Open Source 13.x All Versions
Certified Asterisk 11.6 All Versions
Certified Asterisk 13.8 All VersionsCorrected In
Product Release
Asterisk Open Source 11.23.1, 13.11.1
Certified Asterisk 11.6-cert15, 13.8-cert3Patches
SVN URL RevisionLinks https://issues.asterisk.org/jira/browse/ASTERISK-26272
Asterisk Project Security Advisories are posted at
http://www.asterisk.org/securityThis document may be superseded by later versions; if so, the latest
version will be posted at
http://downloads.digium.com/pub/security/AST-2016-007.pdf and
http://downloads.digium.com/pub/security/AST-2016-007.htmlRevision History
Date Editor Revisions Made
August 23, 2016 Joshua Colp Initial creationAsterisk Project Security Advisory - AST-2016-007
Copyright © 2016 Digium, Inc. All Rights Reserved.
Permission is hereby granted to distribute and publish this advisory in its
original, unaltered form.
AST-2016-006: Crash on ACK from unknown endpoint
Il giorno 08 settembre 2016, l'Asterisk Security Team ha rilasciato il seguente post.
Dal post originale:
Asterisk Project Security Advisory - AST-2016-006Product Asterisk
Summary Crash on ACK from unknown endpoint
Nature of Advisory Remote Crash
Susceptibility Remote unauthenticated sessions
Severity Critical
Exploits Known No
Reported On August 3, 2016
Reported By Nappsoft
Posted On
Last Updated On August 31, 2016
Advisory Contact mark DOT michelson AT digium DOT com
CVE NameDescription Asterisk can be crashed remotely by sending an ACK to it
from an endpoint username that Asterisk does not recognize.
Most SIP request types result in an "artificial" endpoint
being looked up, but ACKs bypass this lookup. The resulting
NULL pointer results in a crash when attempting to
determine if ACLs should be applied.This issue was introduced in the Asterisk 13.10 release and
only affects that release.This issue only affects users using the PJSIP stack with
Asterisk. Those users that use chan_sip are unaffected.Resolution ACKs now result in an artificial endpoint being looked up
just like other SIP request types.Affected Versions
Product Release
Series
Asterisk Open Source 11.x Unaffected
Asterisk Open Source 13.x 13.10.0
Certified Asterisk 11.6 Unaffected
Certified Asterisk 13.8 UnaffectedCorrected In
Product Release
Asterisk Open Source 13.11.1Patches
SVN URL RevisionLinks
Asterisk Project Security Advisories are posted at
http://www.asterisk.org/securityThis document may be superseded by later versions; if so, the latest
version will be posted at
http://downloads.digium.com/pub/security/AST-2016-006.pdf and
http://downloads.digium.com/pub/security/AST-2016-006.htmlRevision History
Date Editor Revisions Made
August 16, 2016 Mark Michelson Initial draft of AdvisoryAsterisk Project Security Advisory - AST-2016-006
Copyright (c) 2016 Digium, Inc. All Rights Reserved.
Permission is hereby granted to distribute and publish this advisory in its
original, unaltered form.
Rilasciato Asterisk 13.11.0
Il giorno 01 settembre 2016, il Team di Sviluppo di Asterisk ha annunciato il rilascio di Asterisk Asterisk 13.11.0.
Dal post originale:
The release of Asterisk 13.11.0 resolves several issues reported by the community and would have not been possible without your participation.
Thank you!
The following are the issues resolved in this release:
New Features made in this release:
-----------------------------------
* ASTERISK-25904 - PJSIP: add contact.updated event (Reported by Alexei Gradinari)
Bugs fixed in this release:
-----------------------------------
* ASTERISK-26269 - res_pjsip: Wrong state for aors without registered contacts after startup (Reported by nappsoft)
* ASTERISK-26299 - app_queue: Queue application sometimes stops calling members with Local interface (Reported by Etienne Lessard)
* ASTERISK-26148 - pjsip: Cannot compile 13.10.0-rc1: "libasteriskpj.so: undefined reference to..." (Reported by Hans van Eijsden)
* ASTERISK-26237 - Fax is detected on regular calls. (Reported by Richard Mudgett)
* ASTERISK-26227 - sqlalchemy error due to long identifier name (Reported by Mark Michelson)
* ASTERISK-19968 - TCP Session-Timers not dropping call (Reported by Aaron Hamstra)
* ASTERISK-26214 - Allow arbitrary time for fax detection to end on a channel (Reported by Richard Mudgett)
* ASTERISK-23013 - [patch] Deadlock between 'sip show channels' command and attended transfer handling (Reported by Ben Smithurst)
* ASTERISK-26216 - res_fax: Deadlock when detect fax while channel executing Playback (Reported by Richard Mudgett)
* ASTERISK-26212 - [patch] Makefile: Retain XML Declaration and DTD in docs. (Reported by Alexander Traud)
* ASTERISK-26211 - Unit tests: AST_TEST_DEFINE should be used in conditional code. (Reported by Corey Farrell)
* ASTERISK-26207 - [patch] sRTP: Count a roll-over of the sequence number even on lost packets. (Reported by Alexander Traud)
* ASTERISK-26038 - 'make install' doesn't seem to install OS/X init files (Reported by Tzafrir Cohen)
* ASTERISK-26200 - [patch] res_pjsip_mwi: improve realtime performance - remove unneeded check on endpoint's contacts. (Reported by Alexei Gradinari)
* ASTERISK-26133 - app_queue: Queue members receive multiple calls (Reported by Richard Miller)
* ASTERISK-26196 - pbx: Time based includes can leak timezone string (Reported by Corey Farrell)
* ASTERISK-26193 - chan_sip: reference leak in mwi_event_cb (Reported by Corey Farrell)
* ASTERISK-25659 - res_rtp_asterisk: ECDH not negotiated causing DTLS failure occurred on RTP instance (Reported by Edwin Vandamme)
* ASTERISK-26191 - threadpool: Leak on duplicate taskprocessor for ast_threadpool_serializer_group (Reported by Corey Farrell)
* ASTERISK-26046 - [patch] Avoid obsolete warnings on autoconf. (Reported by Alexander Traud)
* ASTERISK-26160 - pjsip: Updated->Reachable during qualify (Reported by Matt Jordan)
* ASTERISK-25289 - Build System does not respect CFLAGS and CXXFLAGS when building menuselect (Reported by Jeffrey Walton)
* ASTERISK-26119 - [patch] fix: memory leaks, resource leaks, out of bounds and bugs (Reported by Alexei Gradinari)
* ASTERISK-26177 - func_odbc: Database handle is kept when it should be released (Reported by Leandro Dardini)
* ASTERISK-26184 - chan_sip: Reference leaks in error paths. (Reported by Corey Farrell)
* ASTERISK-26181 - REF_DEBUG: Node object incorrectly logged during duplicate replacement (Reported by Corey Farrell)
* ASTERISK-26180 - PJSIP: provide valid tcp nodelay option for reuse (Reported by Scott Griepentrog)
* ASTERISK-26179 - chan_sip: Second T.38 request fails (Reported by Joshua Colp)
* ASTERISK-26172 - res_sorcery_realtime: fix bug when successful sql UPDATE is treated as failed if there is no affected rows. (Reported by Alexei Gradinari)
* ASTERISK-25772 - res_pjsip: Unexpected two BYE when answered (Reported by Dmitriy Serov)
* ASTERISK-26099 - res_pjsip_pubsub: Crash when sending request due to server timeout (Reported by Ross Beer)
* ASTERISK-26144 - Crash on loading codecs g729/g723 (Reported by Alexei Gradinari)
* ASTERISK-26157 - Build: Fix errors highlighted by GCC 6.x (Reported by George Joseph)
* ASTERISK-26021 - Build codecs siren7 and siren14 for Asterisk 13 (Reported by Daniel Denson)
* ASTERISK-26326 - Crash when dialing MulticastRTP channel (Reported by George Joseph)
Improvements made in this release:
-----------------------------------
* ASTERISK-26220 - Add support for noreturn function attributes. (Reported by Corey Farrell)
* ASTERISK-22131 - Update the make dependencies script to pull, build, and install the correct pjproject (Reported by Matt Jordan)
* ASTERISK-25471 - [patch]Add subscribe_context to res_pjsip (Reported by JoshE)
* ASTERISK-26159 - res_hep: enabled by default and information sent to default address (Reported by Ross Beer)
For a full list of changes in this release, please see the ChangeLog:
http://downloads.asterisk.org/pub/telephony/asterisk/ChangeLog-13.11.0
Rilasciato Asterisk 11.6-cert14
Il giorno 29 agosto 2016, il Team di Sviluppo di Asterisk ha annunciato il rilascio di Asterisk Asterisk 11.6-cert14.
Dal post originale:
The release of Certified Asterisk 11.6-cert14 resolves several issues reported by the community and would have not been possible without your participation.
Thank you!
The following are the issues resolved in this release:
Bugs fixed in this release:
-----------------------------------
* ASTERISK-23013 - [patch] Deadlock between 'sip show channels' command and attended transfer handling (Reported by Ben Smithurst)
* ASTERISK-25494 - build: GCC 5.1.x catches some new const, array bounds and missing paren issues (Reported by George Joseph)
* ASTERISK-24932 - Asterisk 13.x does not build with GCC 5.0 (Reported by Jeffrey C. Ollie)
* ASTERISK-26138 - chan_unistim: Under FreeBSD, chan_unistim generates a compile error (Reported by George Joseph)
* ASTERISK-26157 - Build: Fix errors highlighted by GCC 6.x (Reported by George Joseph)
* ASTERISK-23509 - [patch]SayNumber for Polish language tries to play empty files for numbers divisible by 100 (Reported by zvision)
* ASTERISK-26140 - res_rtp_asterisk: gcc 6 caught a self-comparison (Reported by George Joseph)
* ASTERISK-24436 - Missing header in res/res_srtp.c when compiling against libsrtp-1.5.0 (Reported by Patrick Laimbock)
* ASTERISK-24502 - Build fails when dev-mode, dont optimize and coverage are enabled (Reported by Corey Farrell)
* ASTERISK-26179 - chan_sip: Second T.38 request fails (Reported by Joshua Colp)
* ASTERISK-26034 - T.38 passthrough problem behind firewall due to early nosignal packet (Reported by George Joseph)
* ASTERISK-26030 - call cut because of double Session-Expires header in re-invite after proxy authentication is required (Reported by George Joseph)
For a full list of changes in this release, please see the ChangeLog:
http://downloads.asterisk.org/pub/telephony/certified-asterisk/ChangeLog-certified-11.6-cert14
Rilasciato Asterisk 13.8-cert2
Il giorno 15 agosto 2016, il Team di Sviluppo di Asterisk ha annunciato il rilascio di Asterisk Asterisk 13.8-cert2.
Dal post originale:
The release of Certified Asterisk 13.8-cert2 resolves several issues reported by the community and would have not been possible without your participation.
Thank you!
The following are the issues resolved in this release:
Bugs fixed in this release:
-----------------------------------
* ASTERISK-26280 - DNS lookups can block channel media paths (Reported by Mark Michelson)
* ASTERISK-26132 - PJSIP: provide transport type with received messages (Reported by Scott Griepentrog)
* ASTERISK-26237 - Fax is detected on regular calls. (Reported by Richard Mudgett)
* ASTERISK-23013 - [patch] Deadlock between 'sip show channels' command and attended transfer handling (Reported by Ben Smithurst)
* ASTERISK-26214 - Allow arbitrary time for fax detection to end on a channel (Reported by Richard Mudgett)
For a full list of changes in this release, please see the ChangeLog:
http://downloads.asterisk.org/pub/telephony/certified-asterisk/ChangeLog-certified-13.8-cert2
Rilasciato Asterisk 13.1-cert8
Il giorno 03 agosto 2016, il Team di Sviluppo di Asterisk ha annunciato il rilascio di Asterisk Asterisk 13.1-cert8.
Dal post originale:
he release of Certified Asterisk 13.1-cert8 resolves several issues reported by the community and would have not been possible without your participation.
Thank you!
The following are the issues resolved in this release:
Bugs fixed in this release:
-----------------------------------
* ASTERISK-26179 - chan_sip: Second T.38 request fails (Reported by Joshua Colp)
* ASTERISK-26089 - Invalid security events during boot using PJSIP Realtime (Reported by Scott Griepentrog)
* ASTERISK-26034 - T.38 passthrough problem behind firewall due to early nosignal packet (Reported by George Joseph)
* ASTERISK-26030 - call cut because of double Session-Expires header in re-invite after proxy authentication is required (Reported by George Joseph)
* ASTERISK-25998 - file: Crash when using nativeformats (Reported by Joshua Colp)
* ASTERISK-25337 - Crash on PJSIP_HEADER Add P-Asserted-Identity when calling from Gosub (Reported by Jacques Peacock)
* ASTERISK-25033 - Asterisk 13 (branch head) won't compile without PJSip (Reported by Peter Whisker)
Improvements made in this release:
-----------------------------------
* ASTERISK-26088 - Investigate heavy memory utilization by res_pjsip_pubsub (Reported by Richard Mudgett)
For a full list of changes in this release, please see the ChangeLog:
http://downloads.asterisk.org/pub/telephony/certified-asterisk/ChangeLog-certified-13.1-cert8
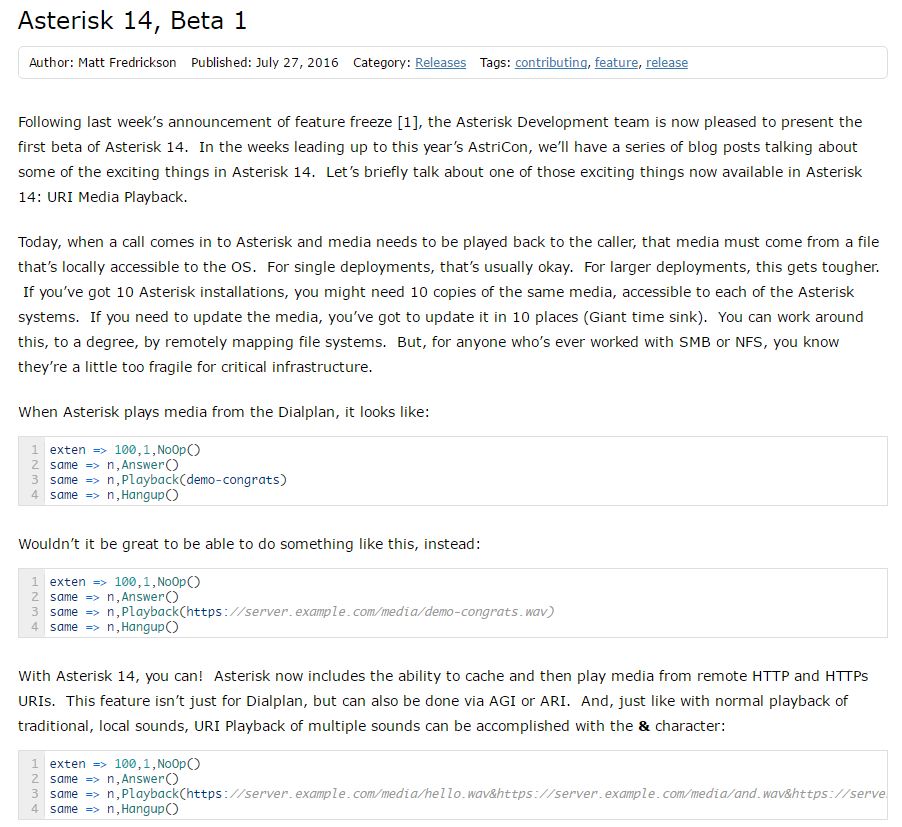
Presentato Asterisk 14 Beta 1
Dal blog.asterisk.org del 27 luglio 2016.
Dal post originale (http://blogs.asterisk.org/2016/07/27/asterisk-14-beta-1/:
Rilasciato Asterisk 13.10.0
Il giorno 21 luglio 2016, il Team di Sviluppo di Asterisk ha annunciato il rilascio di Asterisk Asterisk 13.10.0.
Dal post originale:
The release of Asterisk 13.10.0 resolves several issues reported by the community and would have not been possible without your participation.
Thank you!
The following are the issues resolved in this release:
Improvements made in this release:
-----------------------------------
* ASTERISK-26088 - Investigate heavy memory utilization by res_pjsip_pubsub (Reported by Richard Mudgett)
* ASTERISK-26011 - [patch]PJSIP: add "via_addr", "via_port", "call_id" to contacts (Reported by Alexei Gradinari)
* ASTERISK-25994 - [patch]res_pjsip: module load priority (Reported by Alexei Gradinari)
* ASTERISK-25931 - PJSIP: add "reg_server" to contacts. (Reported by Alexei Gradinari)
* ASTERISK-25835 - Authentication using 'Username' field from Digest (Reported by Ross Beer)
* ASTERISK-25930 - PJSIP: disable multi domain to improve realtime performace (Reported by Alexei Gradinari)
Bugs fixed in this release:
-----------------------------------
* ASTERISK-26160 - pjsip: Updated->Reachable during qualify (Reported by Matt Jordan)
* ASTERISK-26177 - func_odbc: Database handle is kept when it should be released (Reported by Leandro Dardini)
* ASTERISK-26099 - res_pjsip_pubsub: Crash when sending request due to server timeout (Reported by Ross Beer)
* ASTERISK-26141 - res_fax: fax_v21_session_new leaks reference to v21_details (Reported by Corey Farrell)
* ASTERISK-26140 - res_rtp_asterisk: gcc 6 caught a self-comparison (Reported by George Joseph)
* ASTERISK-26138 - chan_unistim: Under FreeBSD, chan_unistim generates a compile error (Reported by George Joseph)
* ASTERISK-26128 - Alembic scripts are failing (Reported by Mark Michelson)
* ASTERISK-26139 - test_res_pjsip_scheduler: Compile failure if pjproject isn't installed in a system location (Reported by George Joseph)
* ASTERISK-26130 - [patch] WebRTC: Should use latest DTLS version. (Reported by Alexander Traud)
* ASTERISK-26127 - res_pjsip_session: Crash due to race condition between res_pjsip_session unload and timer (Reported by Joshua Colp)
* ASTERISK-26083 - ARI: Announcer channels staying around after playback to a bridge is finished (Reported by Per Jensen)
* ASTERISK-26126 - [patch] leverage 'bindaddr' for TLS in http.conf (Reported by Alexander Traud)
* ASTERISK-26069 - Asterisk truncates To: header, dropping the closing '>' (Reported by Vasil Kolev)
* ASTERISK-26097 - [patch] CLI: show maximum file descriptors (Reported by Alexander Traud)
* ASTERISK-25262 - Memory leak when a caller channel does multiple dials and CEL is enabled (Reported by Etienne Lessard)
* ASTERISK-26092 - [Segfault] in res_rtp_asterisk.c:4268 after Remotely bridged channels (Reported by Niklas Larsson)
* ASTERISK-26096 - res_hep: Crash when configuration file is missing (Reported by Niklas Larsson)
* ASTERISK-26089 - Invalid security events during boot using PJSIP Realtime (Reported by Scott Griepentrog)
* ASTERISK-26074 - res_odbc: Deadlock within UnixODBC (Reported by Ross Beer)
* ASTERISK-26054 - Asterisk crashes (core dump) (Reported by B. Davis)
* ASTERISK-24436 - Missing header in res/res_srtp.c when compiling against libsrtp-1.5.0 (Reported by Patrick Laimbock)
* ASTERISK-26091 - [patch] ar cru creates warning, instead use ar cr (Reported by Alexander Traud)
* ASTERISK-26070 - ari/channels: Creating a local channel without an originator adds all audio formats to it's capabilities (Reported by George Joseph)
* ASTERISK-26078 - core: Memory leak in logging (Reported by Etienne Lessard)
* ASTERISK-26065 - chan_pjsip: MWI NOTIFY contents not ordered properly (Reported by Ross Beer)
* ASTERISK-26063 - ${PJSIP_HEADER(read,Call-ID)} does not work - documentation needs clarification for when read/write is possible (Reported by Private Name)
* ASTERISK-25777 - data race in threadpool (Reported by Badalian Vyacheslav)
* ASTERISK-26038 - 'make install' doesn't seem to install OS/X init files (Reported by Tzafrir Cohen)
* ASTERISK-26029 - parking: ast_parking_park_call should return parking_space instead of parking_exten (Reported by Diederik de Groot)
* ASTERISK-25938 - res_odbc: MySQL/MariaDB statement LAST_INSERT_ID() always returns zero. (Reported by Edwin Vandamme)
* ASTERISK-25941 - chan_pjsip: Crash on an immediate SIP final response (Reported by Javier Riveros )
* ASTERISK-26014 - res_sorcery_astdb: Make tolerant of unknown fields (Reported by Joshua Colp)
* ASTERISK-24986 - keepalive INFO packages ignored by asterisk (Reported by Ilya Trikoz)
* ASTERISK-26034 - T.38 passthrough problem behind firewall due to early nosignal packet (Reported by George Joseph)
* ASTERISK-26030 - call cut because of double Session-Expires header in re-invite after proxy authentication is required (Reported by George Joseph)
* ASTERISK-25964 - Outbound registrations created via ARI/push configuration do not clean up outbound registrations currently in flight (Reported by Matt Jordan)
* ASTERISK-26005 - res_pjsip: Multiple SIP messages are combined into 1 TCP packet (Reported by Ross Beer)
* ASTERISK-25352 - res_hep_rtcp correlation_id is different then res_hep (Reported by Kevin Scott Adams)
* ASTERISK-26008 - app_followme does not delete recorded name prompt (Reported by Tzafrir Cohen)
* ASTERISK-26007 - res_pjsip: Endpoints deleting early after upgrade from 13.8.2 to 13.9 (Reported by Greg Siemon)
* ASTERISK-25990 - PJSIP TLS registration should respect client_uri scheme when generating Contact URI (Reported by Sebastian Damm)
* ASTERISK-25978 - res_pjsip_authenticator_digest: Should not use source port in nonce verification (Reported by Mark Michelson)
* ASTERISK-25993 - pjproject: Allow bundling to not require everything it does (Reported by Joshua Colp)
* ASTERISK-25956 - Compilation error in conditionally compiled code in config_options.c (Reported by Chris Trobridge)
* ASTERISK-25998 - file: Crash when using nativeformats (Reported by Joshua Colp)
* ASTERISK-25826 - PJSIP / Sorcery slow load from realtime (Reported by Ross Beer)
* ASTERISK-25968 - pjproject_bundled: Configure and make need to be re-tested (Reported by George Joseph)
* ASTERISK-24463 - Voicemail email address corrupt or not sent when message is in the process of being recorded during reload (Reported by John Campbell)
* ASTERISK-25970 - Segfault in pjsip_url_compare (Reported by Dmitriy Serov)
* ASTERISK-25963 - func_odbc requires reconnect checks for stale connections (Reported by Ross Beer)
* ASTERISK-25961 - tests/channels/SIP/sip_tls_call: Sporadic crash when running test (Reported by Joshua Colp)
* ASTERISK-16115 - [patch] problem with ringinuse=no, queue members receive sometimes two calls (Reported by nik600)
* ASTERISK-25917 - [patch]app_voicemail: passwordlocation=spooldir only works if you manually add secret.conf yourself (Reported by Jonathan R. Rose)
* ASTERISK-25950 - [patch]SIP channel does not send PeerStatus events for autocreated peers (Reported by Kirill Katsnelson)
* ASTERISK-25954 - Manager QueueSummary and QueueStatus Actions are case sensitive to QueueName (Reported by Javier Acosta)
New Features made in this release:
-----------------------------------
* ASTERISK-25904 - PJSIP: add contact.updated event (Reported by Alexei Gradinari)
For a full list of changes in this release, please see the ChangeLog:
http://downloads.asterisk.org/pub/telephony/asterisk/ChangeLog-13.10.0
Rilasciato Asterisk 11.23.0
Il giorno 21 luglio 2016, il Team di Sviluppo di Asterisk ha annunciato il rilascio di Asterisk Asterisk 11.23.0.
Dal post originale:
The release of Asterisk 11.23.0 resolves several issues reported by the community and would have not been possible without your participation.
Thank you!
The following are the issues resolved in this release:
Bugs fixed in this release:
-----------------------------------
* ASTERISK-26141 - res_fax: fax_v21_session_new leaks reference to v21_details (Reported by Corey Farrell)
* ASTERISK-26140 - res_rtp_asterisk: gcc 6 caught a self-comparison (Reported by George Joseph)
* ASTERISK-26138 - chan_unistim: Under FreeBSD, chan_unistim generates a compile error (Reported by George Joseph)
* ASTERISK-26130 - [patch] WebRTC: Should use latest DTLS version. (Reported by Alexander Traud)
* ASTERISK-26126 - [patch] leverage 'bindaddr' for TLS in http.conf (Reported by Alexander Traud)
* ASTERISK-26069 - Asterisk truncates To: header, dropping the closing '>' (Reported by Vasil Kolev)
* ASTERISK-26097 - [patch] CLI: show maximum file descriptors (Reported by Alexander Traud)
* ASTERISK-24436 - Missing header in res/res_srtp.c when compiling against libsrtp-1.5.0 (Reported by Patrick Laimbock)
* ASTERISK-26091 - [patch] ar cru creates warning, instead use ar cr (Reported by Alexander Traud)
* ASTERISK-26038 - 'make install' doesn't seem to install OS/X init files (Reported by Tzafrir Cohen)
* ASTERISK-26034 - T.38 passthrough problem behind firewall due to early nosignal packet (Reported by George Joseph)
* ASTERISK-26030 - call cut because of double Session-Expires header in re-invite after proxy authentication is required (Reported by George Joseph)
* ASTERISK-26008 - app_followme does not delete recorded name prompt (Reported by Tzafrir Cohen)
* ASTERISK-24463 - Voicemail email address corrupt or not sent when message is in the process of being recorded during reload (Reported by John Campbell)
* ASTERISK-25917 - [patch]app_voicemail: passwordlocation=spooldir only works if you manually add secret.conf yourself (Reported by Jonathan R. Rose)
* ASTERISK-25954 - Manager QueueSummary and QueueStatus Actions are case sensitive to QueueName (Reported by Javier Acosta)
* ASTERISK-16115 - [patch] problem with ringinuse=no, queue members receive sometimes two calls (Reported by nik600)
* ASTERISK-25934 - chan_sip should not require sipregs or updateable sippeers table unless rt (Reported by Jaco Kroon)
* ASTERISK-25888 - Frequent segfaults in function can_ring_entry() of app_queue.c (Reported by Sébastien Couture)
* ASTERISK-25874 - app_voicemail: Stack buffer overflow in test_voicemail_notify_endl (Reported by Badalian Vyacheslav)
* ASTERISK-25912 - chan_local passes AST_CONTROL_PVT_CAUSE_CODE without adding them to the local hangupcauses via ast_channel_hangupcause_hash_set (Reported by Jaco Kroon)
* ASTERISK-25407 - Asterisk fails to log to multiple syslog destinations (Reported by Elazar Broad)
* ASTERISK-25510 - [patch]Log to syslog failing (Reported by Michael Newton)
Improvements made in this release:
-----------------------------------
* ASTERISK-25444 - [patch]Music On Hold Warning misleading (Reported by Conrad de Wet)
For a full list of changes in this release, please see the ChangeLog:
http://downloads.asterisk.org/pub/telephony/asterisk/ChangeLog-11.23.0
Rilasciato Asterisk 13.8-cert1
Il giorno 13 luglio 2016, il Team di Sviluppo di Asterisk ha annunciato il rilascio di Asterisk Asterisk 13.8-cert1.
Dal post originale:
The release of Certified Asterisk 13.8-cert1 resolves several issues reported by the
community and would have not been possible without your participation.
Thank you!
The following are the issues resolved in this release:
New Features made in this release:
-----------------------------------
* ASTERISK-24919 - res_pjsip_config_wizard: Ability to write contents to file (Reported by Ray Crumrine)
* ASTERISK-25670 - Add regcontext to PJSIP (Reported by Daniel Journo)
* ASTERISK-25480 - [patch]Add field PauseReason on QueueMemberStatus (Reported by Rodrigo Ramirez Norambuena)
* ASTERISK-25419 - Dialplan Application for Integration of StatsD (Reported by Ashley Sanders)
* ASTERISK-25549 - Confbridge: Add participant timeout option (Reported by Mark Michelson)
* ASTERISK-24922 - ARI: Add the ability to intercept hold and raise an event (Reported by Matt Jordan)
* ASTERISK-25377 - res_pjsip: Change default "From user" from UUID to something more palatable (Reported by Mark Michelson)
* ASTERISK-25252 - ARI: Add the ability to manipulate log channels (Reported by Matt Jordan)
* ASTERISK-25259 - chan_pjsip: Add rtptimeout support (Reported by Joshua Colp)
* ASTERISK-25238 - ARI: Support push configuration (Reported by Matt Jordan)
* ASTERISK-25173 - ARI: Add the ability to load/reload/unload an Asterisk module (Reported by Matt Jordan)
* ASTERISK-17899 - Handle crypto lifetime in SDES-SRTP negotiation (Reported by Dwayne Hubbard)
* ASTERISK-24703 - ARI: Add the ability to "transfer" (redirect) a channel (Reported by Matt Jordan)
Bugs fixed in this release:
-----------------------------------
* ASTERISK-26179 - chan_sip: Second T.38 request fails (Reported by Joshua Colp)
* ASTERISK-26140 - res_rtp_asterisk: gcc 6 caught a self-comparison (Reported by George Joseph)
* ASTERISK-26099 - res_pjsip_pubsub: Crash when sending request due to server timeout (Reported by Ross Beer)
* ASTERISK-26157 - Build: Fix errors highlighted by GCC 6.x (Reported by George Joseph)
* ASTERISK-26089 - Invalid security events during boot using PJSIP Realtime (Reported by Scott Griepentrog)
* ASTERISK-25885 - res_pjsip: Race condition between adding contact and automatic expiration (Reported by Joshua Colp)
* ASTERISK-26074 - res_odbc: Deadlock within UnixODBC (Reported by Ross Beer)
* ASTERISK-26054 - Asterisk crashes (core dump) (Reported by B. Davis)
* ASTERISK-26034 - T.38 passthrough problem behind firewall due to early nosignal packet (Reported by George Joseph)
* ASTERISK-26030 - call cut because of double Session-Expires header in re-invite after proxy authentication is required (Reported by George Joseph)
* ASTERISK-26004 - res_pjsip: The transport/method parameter is ignored (Reported by George Joseph)
* ASTERISK-25978 - res_pjsip_authenticator_digest: Should not use source port in nonce verification (Reported by Mark Michelson)
* ASTERISK-25998 - file: Crash when using nativeformats (Reported by Joshua Colp)
* ASTERISK-16115 - [patch] problem with ringinuse=no, queue members receive sometimes two calls (Reported by nik600)
* ASTERISK-25951 - res_agi: run_agi eats frames it shouldn't (Reported by George Joseph)
* ASTERISK-25947 - Protocol transfers to stasis applications are missing the StasisStart with the replace_channel object. (Reported by Richard Mudgett)
* ASTERISK-24649 - Pushing of channel into bridge fails; Stasis fails to get app name (Reported by John Bigelow)
* ASTERISK-24782 - StasisEnd event not present for channel that was swapped out for another after completing attended transfer (Reported by John Bigelow)
* ASTERISK-25942 - res_pjsip_caller_id: Transfer results in mixed ConnectedLine information (Reported by George Joseph)
* ASTERISK-25928 - res_pjsip: URI validation done outside of PJSIP thread (Reported by Joshua Colp)
* ASTERISK-25929 - res_pjsip_registrar: AOR_CONTACT_ADDED events not raised (Reported by Joshua Colp)
* ASTERISK-25796 - res_pjsip: DOS/Crash when TCP/TLS sockets exceed pjproject PJ_IOQUEUE_MAX_HANDLES (Reported by George Joseph)
* ASTERISK-25707 - Long contact URIs or hostnames can crash pjproject/Asterisk under certain conditions (Reported by George Joseph)
* ASTERISK-25854 - No audio after HOLD/RESUME - incorrect a=recvonly in SDP from Asterisk (Reported by Robert McGilvray)
* ASTERISK-25882 - ARI: Crash can occur due to race condition when attempting to operate on a hung up channel (Part 2) (Reported by Richard Mudgett)
* ASTERISK-25849 - chan_pjsip: transfers with direct media sometimes drops audio (Reported by Kevin Harwell)
* ASTERISK-25113 - install_prereq in Debian 8 without "standard system utilities" (Reported by Rodrigo Ramirez Norambuena)
* ASTERISK-25814 - Segfault at f ip in res_pjsip_refer.so (Reported by Sergio Medina Toledo)
* ASTERISK-25023 - Deadlock in chan_sip in update_provisional_keepalive (Reported by Arnd Schmitter)
* ASTERISK-25321 - [patch]DeadLock ChanSpy with call over Local channel (Reported by Filip Frank)
* ASTERISK-25829 - res_pjsip: PJSIP does not accept spaces when separating multiple AORs (Reported by Mateusz Kowalski)
* ASTERISK-25771 - ARI:Crash - Attended transfers of channels into Stasis application. (Reported by Javier Riveros )
* ASTERISK-25830 - Revision 2451d4e breaks NAT (Reported by Sean Bright)
* ASTERISK-25582 - Testsuite: Reactor timeout error in tests/fax/pjsip/directmedia_reinvite_t38 (Reported by Matt Jordan)
* ASTERISK-25811 - Unable to delete object from sorcery cache (Reported by Ross Beer)
* ASTERISK-25800 - [patch] Calculate talktime when is first call answered (Reported by Rodrigo Ramirez Norambuena)
* ASTERISK-25727 - RPM build requires OPTIONAL_API cflag due to PJSIP requirement (Reported by Gergely Dömsödi)
* ASTERISK-25337 - Crash on PJSIP_HEADER Add P-Asserted-Identity when calling from Gosub (Reported by Jacques Peacock)
* ASTERISK-25738 - res_pjsip_pubsub: Crash while executing OutboundSubscriptionDetail ami action (Reported by Kevin Harwell)
* ASTERISK-25721 - [patch] res_phoneprov: memory leak and heap-use-after-free (Reported by Badalian Vyacheslav)
* ASTERISK-25272 - [patch]The ICONV dialplan function sometimes returns garbage (Reported by Etienne Lessard)
* ASTERISK-25751 - res_pjsip: Support pjsip_dlg_create_uas_and_inc_lock (Reported by Joshua Colp)
* ASTERISK-25606 - Core dump when using transports in sorcery (Reported by Martin MouÄka)
* ASTERISK-20987 - non-admin users, who join muted conference are not being muted (Reported by hristo)
* ASTERISK-25737 - res_pjsip_outbound_registration: line option not in Alembic (Reported by Joshua Colp)
* ASTERISK-25603 - [patch]udptl: Uninitialized lengths and bufs in udptl_rx_packet cause ast_frdup crash (Reported by Walter Doekes)
* ASTERISK-25742 - Secondary IFP Packets can result in accessing uninitialized pointers and a crash (Reported by Torrey Searle)
* ASTERISK-24972 - Transport Layer Security (TLS) Protocol BEAST Vulnerability - Investigate vulnerability of HTTP server (Reported by Alex A. Welzl)
* ASTERISK-25397 - [patch]chan_sip: File descriptor leak with non-default timert1 (Reported by Alexander Traud)
* ASTERISK-25702 - PjSip realtime DB and Cache Errors since upgrade to asterisk-13.7.0 from asterisk-13.7.0-rc2 (Reported by Nic Colledge)
* ASTERISK-25730 - build: make uninstall after make distclean tries to remove root (Reported by George Joseph)
* ASTERISK-25725 - core: Incorrect XML documentation may result in weird behavior (Reported by Joshua Colp)
* ASTERISK-25722 - ASAN & testsute: stack-buffer-overflow in sip_sipredirect (Reported by Badalian Vyacheslav)
* ASTERISK-25709 - ARI: Crash can occur due to race condition when attempting to operate on a hung up channel (Reported by Mark Michelson)
* ASTERISK-25714 - ASAN:heap-buffer-overflow in logger.c (Reported by Badalian Vyacheslav)
* ASTERISK-25685 - infrastructure: Run alembic in Jenkins build script (Reported by Joshua Colp)
* ASTERISK-25712 - Second call to already-on-call phone and Asterisk sends "Ready" (Reported by Richard Mudgett)
* ASTERISK-24801 - ASAN: ast_el_read_char stack-buffer-overflow (Reported by Badalian Vyacheslav)
* ASTERISK-25179 - CDR(billsec,f) and CDR(duration,f) report incorrect values (Reported by Gianluca Merlo)
* ASTERISK-25611 - core: threadpool thread_timeout_thrash unit test sporadically failing (Reported by Joshua Colp)
* ASTERISK-24097 - Documentation - CHANNEL function help text missing 'linkedid' argument (Reported by Steven T. Wheeler)
* ASTERISK-25700 - main/config: Clean config maps on shutdown. (Reported by Corey Farrell)
* ASTERISK-25696 - bridge_basic: don't cache xferfailsound during a transfer (Reported by Kevin Harwell)
* ASTERISK-25697 - bridge_basic: don't play an attended transfer fail sound after target hangs up (Reported by Kevin Harwell)
* ASTERISK-25683 - res_ari: Asterisk fails to start if compiled with MALLOC_DEBUG (Reported by yaron nahum)
* ASTERISK-25686 - PJSIP: qualify_timeout is a double, database schema is an integer (Reported by Marcelo Terres)
* ASTERISK-25690 - Hanging up when executing connected line sub does not cause hangup (Reported by Joshua Colp)
* ASTERISK-25687 - res_musiconhold: Concurrent invocations of 'moh reload' cause a crash (Reported by Sean Bright)
* ASTERISK-25632 - res_pjsip_sdp_rtp: RTP is sent from wrong IP address when multihomed (Reported by Olivier Krief)
* ASTERISK-25637 - Multi homed server using wrong IP (Reported by Daniel Journo)
* ASTERISK-25394 - pbx: Incorrect device and presence state when changing hint details (Reported by Joshua Colp)
* ASTERISK-25640 - pbx: Deadlock on features reload and state change hint. (Reported by Krzysztof Trempala)
* ASTERISK-25681 - devicestate: Engine thread is not shut down (Reported by Corey Farrell)
* ASTERISK-25680 - manager: manager_channelvars is not cleaned at shutdown (Reported by Corey Farrell)
* ASTERISK-25679 - res_calendar leaks scheduler. (Reported by Corey Farrell)
* ASTERISK-25675 - Endpoint not listed as Unreachable (Reported by Daniel Journo)
* ASTERISK-25677 - pbx_dundi: leaks during failed load. (Reported by Corey Farrell)
* ASTERISK-25673 - res_crypto leaks CLI entries (Reported by Corey Farrell)
* ASTERISK-25668 - res_pjsip: Deadlock in distributor (Reported by Mark Michelson)
* ASTERISK-25664 - ast_format_cap_append_by_type leaks a reference (Reported by Corey Farrell)
* ASTERISK-25647 - bug of cel_radius.c: wrong point of ADD_VENDOR_CODE (Reported by Aaron An)
* ASTERISK-25317 - asterisk sends too many stun requests (Reported by Stefan Engström)
* ASTERISK-25137 - endpoint stasis messages are delivered twice (Reported by Vitezslav Novy)
* ASTERISK-25116 - res_pjsip: Two PeerStatus AMI messages are sent for every status change (Reported by George Joseph)
* ASTERISK-25641 - bridge: GOTO_ON_BLINDXFR doesn't work on transfer initiated channel (Reported by Dmitry Melekhov)
* ASTERISK-25614 - DTLS negotiation delays (Reported by Dade Brandon)
* ASTERISK-25442 - using realtime (mysql) queue members are never updated in wait_our_turn function (app_queue.c) (Reported by Carlos Oliva)
* ASTERISK-25625 - res_sorcery_memory_cache: Add full backend caching (Reported by Joshua Colp)
* ASTERISK-25601 - json: Audit reference usage and thread safety (Reported by Joshua Colp)
* ASTERISK-25615 - res_pjsip: Setting transport async_operations > 1 causes segfault on tls transports (Reported by George Joseph)
* ASTERISK-25364 - [patch]Issue a TCP connection(kernel) and thread of asterisk is not released (Reported by Hiroaki Komatsu)
* ASTERISK-25624 - AMI Event OriginateResponse bug (Reported by sungtae kim)
* ASTERISK-25619 - res_chan_stats not sending the correct information to StatsD (Reported by Tyler Cambron)
* ASTERISK-25569 - app_meetme: Audio quality issues (Reported by Corey Farrell)
* ASTERISK-25609 - [patch]Asterisk may crash when calling ast_channel_get_t38_state(c) (Reported by Filip Jenicek)
* ASTERISK-24146 - [patch]No audio on WebRtc caller side when answer waiting time is more than ~7sec (Reported by Aleksei Kulakov)
* ASTERISK-25599 - [patch] SLIN Resampling Codec only 80 msec (Reported by Alexander Traud)
* ASTERISK-25616 - Warning with a Codec Module which supports PLC with FEC (Reported by Alexander Traud)
* ASTERISK-25610 - Asterisk crash during "sip reload" (Reported by Dudás József)
* ASTERISK-25608 - res_pjsip/contacts/statsd: Lifecycle events aren't consistent (Reported by George Joseph)
* ASTERISK-25584 - [patch] format-attribute module: VP8 missing (Reported by Alexander Traud)
* ASTERISK-25583 - [patch] format-attribute module: RFC 7587 (Opus Codec) (Reported by Alexander Traud)
* ASTERISK-25498 - Asterisk crashes when negotiating g729 without that module installed (Reported by Ben Langfeld)
* ASTERISK-25595 - Unescaped : in messge sent to statsd (Reported by Niklas Larsson)
* ASTERISK-25476 - chan_sip loses registrations after a while (Reported by Michael Keuter)
* ASTERISK-25598 - res_pjsip: Contact status messages are printing a hash instead of the uri (Reported by George Joseph)
* ASTERISK-25600 - bridging: Inconsistency in BRIDGEPEER (Reported by Jonathan Rose)
* ASTERISK-25593 - fastagi: record file closed after sending result (Reported by Kevin Harwell)
* ASTERISK-25585 - [patch]rasterisk never hits most of main(), but it's assumed to (Reported by Walter Doekes)
* ASTERISK-25590 - CLI Usage info for 'pjsip send notify' references incorrect config (Reported by Corey Farrell)
* ASTERISK-25165 - Testsuite - Sorcery memory cache leaks (Reported by Corey Farrell)
* ASTERISK-25575 - res_pjsip: Dynamic outbound registrations created via ARI are not loaded into memory on Asterisk start/restart (Reported by Matt Jordan)
* ASTERISK-25545 - [patch] translation module gets cached not joint format (Reported by Alexander Traud)
* ASTERISK-25573 - [patch] H.264 format attribute module: resets whole SDP (Reported by Alexander Traud)
* ASTERISK-24958 - Forwarding loop detection inhibits certain desirable scenarios (Reported by Mark Michelson)
* ASTERISK-25561 - app_queue.c line 6503 (try_calling): mutex 'qe->chan' freed more times than we've locked! (Reported by Alec Davis)
* ASTERISK-25552 - hashtab: Improve NULL tolerance (Reported by Joshua Colp)
* ASTERISK-25160 - [patch] Opus Codec: SIP/SDP line fmtp missing when called internally (Reported by Alexander Traud)
* ASTERISK-25535 - [patch] format creation on module load instead of cache (Reported by Alexander Traud)
* ASTERISK-25449 - main/sched: Regression introduced by 5c713fdf18f causes erroneous duplicate RTCP messages; other potential scheduling issues in chan_sip/chan_skinny (Reported by Matt Jordan)
* ASTERISK-25546 - threadpool: Race condition between idle timeout and activation (Reported by Joshua Colp)
* ASTERISK-25537 - [patch] format-attribute module: RFC or internal defaults? (Reported by Alexander Traud)
* ASTERISK-25533 - [patch] buffer for ast_format_cap_get_names only 64 bytes (Reported by Alexander Traud)
* ASTERISK-25373 - add documentation for CALLERID(pres) and also the CONNECTEDLINE and REDIRECTING variants (Reported by Walter Doekes)
* ASTERISK-25527 - Quirky xmldoc description wrapping (Reported by Walter Doekes)
* ASTERISK-24779 - Passthrough OPUS codec not working with chan_pjsip (Reported by PowerPBX)
* ASTERISK-25522 - ARI: Crash when creating channel via ARI originate with requesting channel (Reported by Matt Jordan)
* ASTERISK-25434 - Compiler flags not reported in 'core show settings' despite usage during compilation (Reported by Rusty Newton)
* ASTERISK-24106 - WebSockets Automatically decides what driver it will use (Reported by Andrew Nagy)
* ASTERISK-25513 - Crash: malloc failed with high load of subscriptions. (Reported by John Bigelow)
* ASTERISK-25505 - res_pjsip_pubsub: Crash on off-nominal when UAS dialog can't be created (Reported by Joshua Colp)
* ASTERISK-24543 - Asterisk 13 responds to SIP Invite with all possible codecs configured for peer as opposed to intersection of configured codecs and offered codecs (Reported by Taylor Hawkes)
* ASTERISK-25494 - build: GCC 5.1.x catches some new const, array bounds and missing paren issues (Reported by George Joseph)
* ASTERISK-25485 - res_pjsip_outbound_registration: registration stops due to 400 response (Reported by Kevin Harwell)
* ASTERISK-25486 - res_pjsip: Fix deadlock when validating URIs (Reported by Joshua Colp)
* ASTERISK-7803 - [patch] Update the maximum packetization values in frame.c (Reported by dea)
* ASTERISK-25484 - [patch] autoframing=yes has no effect (Reported by Alexander Traud)
* ASTERISK-25461 - Nested dialplan #includes don't work as expected. (Reported by Richard Mudgett)
* ASTERISK-25455 - Deadlock of PJSIP realtime over res_config_pgsql (Reported by mdu113)
* ASTERISK-25135 - [patch]RTP Timeout hangup cause code missing (Reported by Olle Johansson)
* ASTERISK-25435 - Asterisk periodically hangs. UDP Recv-Q greatly exceeds zero. (Reported by Dmitriy Serov)
* ASTERISK-25451 - Broken video - erased rtp marker bit (Reported by Stefan Engström)
* ASTERISK-25400 - Hints broken when "CustomPresence" doesn't exist in AstDB (Reported by Andrew Nagy)
* ASTERISK-25443 - [patch]IPv6 - Potential issue in via header parsing (Reported by ffs)
* ASTERISK-25404 - segfault/crash in chan_pjsip_hangup ... at chan_pjsip.c (Reported by Chet Stevens)
* ASTERISK-25391 - AMI GetConfigJSON returns invalid JSON (Reported by Bojan NemÄić)
* ASTERISK-25441 - Deadlock in res_sorcery_memory_cache. (Reported by Richard Mudgett)
* ASTERISK-25438 - res_rtp_asterisk: ICE role message even when ICE is not enabled (Reported by Joshua Colp)
* ASTERISK-25383 - Core dumps on startup and shutdown with MALLOC_DEBUG enabled (Reported by yaron nahum)
* ASTERISK-25423 - Caller gets no Connected line update during call pickup. (Reported by Richard Mudgett)
* ASTERISK-25305 - Dynamic logger channels can be added multiple times (Reported by Mark Michelson)
* ASTERISK-25418 - On-hold channels redirected out of a bridge appear to still be on hold (Reported by Mark Michelson)
* ASTERISK-25384 - Regular Asterisk crashes when using Page application. "user_data is NULL" (Reported by Chet Stevens)
* ASTERISK-25407 - Asterisk fails to log to multiple syslog destinations (Reported by Elazar Broad)
* ASTERISK-25410 - app_record: RECORDED_FILE variable not being populated (Reported by Kevin Harwell)
* ASTERISK-25396 - chan_sip: Extremely long callerid name causes invalid SIP (Reported by Walter Doekes)
* ASTERISK-25399 - app_queue: AgentComplete event has wrong reason (Reported by Kevin Harwell)
* ASTERISK-25185 - Segfault in app_queue on transfer scenarios (Reported by Etienne Lessard)
* ASTERISK-25353 - [patch] Transcoding while different in Frame size = Frames lost (Reported by Alexander Traud)
* ASTERISK-25325 - ARI PUT reload chan_sip HTTP response 404 (Reported by Rodrigo Ramirez Norambuena)
* ASTERISK-25390 - default_from_user can crash with certain configuration backends (Reported by Mark Michelson)
* ASTERISK-25387 - res_pjsip_nat: Malformed REGISTER request causes NAT'd Contact header to not be rewritten (Reported by Matt Jordan)
* ASTERISK-25227 - No audio at in-band announcements in ooh323 channel (Reported by Alexandr Dranchuk)
* ASTERISK-25369 - res_parking: ParkAndAnnounce - Inheritable variables aren't applied to the announcer channel (Reported by Jonathan Rose)
* ASTERISK-25295 - res_pjsip crash - pjsip_uri_get_uri at /usr/include/pjsip/sip_uri.h (Reported by Dmitriy Serov)
* ASTERISK-25381 - res_pjsip: AoRs deleted via ARI (or other mechanism) do not destroy their related contacts (Reported by Matt Jordan)
* ASTERISK-25352 - res_hep_rtcp correlation_id is different then res_hep (Reported by Kevin Scott Adams)
* ASTERISK-25367 - pbx: Long pattern match hints may cause "core show hints" to crash (Reported by Joshua Colp)
* ASTERISK-25365 - Persistent subscriptions have extra Content-Length/corrupted messages (Reported by Mark Michelson)
* ASTERISK-25362 - Deadlock due to presence state callback (Reported by Mark Michelson)
* ASTERISK-25356 - res_pjsip_sdp_rtp: Multiple keepalive scheduled items may exist (Reported by Joshua Colp)
* ASTERISK-25355 - sched: ast_sched_del may return prematurely due to spurious wakeup (Reported by Joshua Colp)
* ASTERISK-25318 - tests/rest_api/applications/subscribe-endpoint/nominal/resource: Sporadically failing (Reported by Joshua Colp)
* ASTERISK-25346 - chan_sip: Overwriting answered elsewhere hangup cause on call pickup (Reported by Joshua Colp)
* ASTERISK-25342 - res_pjsip: Repeated usage of pj_gethostip may block (Reported by Joshua Colp)
* ASTERISK-25341 - bridge: Hangups may get lost when executing actions (Reported by Joshua Colp)
* ASTERISK-25339 - res_pjsip: Empty "auth" sections from non-config backgrounds are interpreted as valid (Reported by Matt Jordan)
* ASTERISK-25215 - Differences in queue.log between Set QUEUE_MEMBER and using PauseQueueMember (Reported by Lorne Gaetz)
* ASTERISK-25322 - Crash occurs when using MixMonitor with t() or r() options. (Reported by Richard Mudgett)
* ASTERISK-25320 - chan_sip.c: sip_report_security_event searches for wrong or non existent peer on invite (Reported by Kevin Harwell)
* ASTERISK-25315 - DAHDI channels send shortened duration DTMF tones. (Reported by Richard Mudgett)
* ASTERISK-25312 - res_http_websocket: Terminate connection on fatal cases (Reported by Joshua Colp)
* ASTERISK-25306 - Persistent subscriptions can save multiple SIP messages at once, leading to potential crashes. (Reported by Mark Michelson)
* ASTERISK-25309 - [patch] iLBC 20 advertised (Reported by Alexander Traud)
* ASTERISK-25304 - res_pjsip: XML sanitization may write past buffer (Reported by Joshua Colp)
* ASTERISK-25265 - [patch]DTLS Failure when calling WebRTC-peer on Firefox 39 - add ECDH support and fallback to prime256v1 (Reported by Stefan Engström)
* ASTERISK-25296 - RTP performance issue with several channel drivers. (Reported by Richard Mudgett)
* ASTERISK-25297 - Crashes running channels/pjsip/resolver/srv/failover/in_dialog testsuite tests (Reported by Richard Mudgett)
* ASTERISK-25292 - Testuite: tests/apps/bridge/bridge_wait/bridge_wait_e_options fails (Reported by Kevin Harwell)
* ASTERISK-25271 - Parking & blind transfer: Transferer channel not hung up if no MOH (Reported by Kevin Harwell)
* ASTERISK-25250 - chan_sip - Despite the channel being answered, caller on a call established via Local channel continues to hear ringback (Reported by Etienne Lessard)
* ASTERISK-25253 - confbridge volume options and other volume controls such as func_volume don't work (Reported by Dmitriy Serov)
* ASTERISK-25247 - choppy audio when spying on a g722 channel, chan_sip or chan_pjsip (Reported by hristo)
* ASTERISK-24867 - Docs for 'e' option in ResetCDR say to use CDR_PROP instead, CDR_PROP docs are unclear (Reported by Rusty Newton)
* ASTERISK-24853 - Documentation claims chan_sip outbound registrations support WS or WSS as valid transports (not true) (Reported by PSDK)
* ASTERISK-25242 - PJSIP: No audio when Asterisk inside NAT and endpoints outside NAT - implement functionality similar to chan_sip 'rtpkeepalive'? (Reported by Mark Michelson)
* ASTERISK-25258 - chan_pjsip: Incorrect format switch on received RTP packet (Reported by Joshua Colp)
* ASTERISK-25257 - [patch]channels/sig_pri.h -> sig_pri_span -> force_restart_unavailable_chans in wrong scope (Reported by Patric Marschall)
* ASTERISK-24934 - [patch]Asterisk manager output does not escape control characters (Reported by warren smith)
* ASTERISK-25255 - Missing AMI VarSet events when setting to an empty string. (Reported by Richard Mudgett)
* ASTERISK-25254 - Crash if dialplan sets ATTENDEDTRANSFER to an empty string before Park. (Reported by Richard Mudgett)
* ASTERISK-25183 - PJSIP: Crash on NULL channel in chan_pjsip_incoming_response despite previous checks for NULL channel (Reported by Matt Jordan)
* ASTERISK-25201 - Crash in PJSIP distributor on already free'd threadpool (Reported by Matt Jordan)
* ASTERISK-25240 - bridge_native_rtp: Direct media wrongfully started when completing attended transfer (Reported by Joshua Colp)
* ASTERISK-25103 - Roundup - investigate Asterisk DTLS crashes (Reported by Rusty Newton)
* ASTERISK-22805 - res_rtp_asterisk: Crash when calling BIO_ctrl_pending in dtls_srtp_check_pending when dialed by JSSIP (Reported by Dmitry Burilov)
* ASTERISK-24550 - res_rtp_asterisk: Crash in ast_rtp_on_ice_complete during DTLS handshake (Reported by Osaulenko Alexander)
* ASTERISK-24651 - [patch] Fix race condition in DTLS (Reported by Badalian Vyacheslav)
* ASTERISK-24832 - [patch]DTLS-crashes within openssl (Reported by Stefan Engström)
* ASTERISK-25127 - DTLS crashes following "Unable to cancel schedule ID" in dtls_srtp_check_pending (Reported by Dade Brandon)
* ASTERISK-25168 - Random Core Dumps on Asterisk 13.4 PJSIP, in ast_channel_name at channel_internal_api.c (Reported by Carl Fortin)
* ASTERISK-25115 - Crash related to func sip_resolve_invoke_user_callback of res_pjsip/pjsip_resolver.c (Reported by John Bigelow)
* ASTERISK-25226 - chan_sip: Channel leak in branch 13 on early replaces call pickup (Reported by Walter Doekes)
* ASTERISK-25220 - [patch]Closing of fd -1 in chan_mgcp.c (Reported by Walter Doekes)
* ASTERISK-25219 - [patch]Source and destination overlap in memcpy in rtp_engine.c (Reported by Walter Doekes)
* ASTERISK-25212 - [patch]Segfault when using DEBUG_FD_LEAKS (Reported by Walter Doekes)
* ASTERISK-19277 - [patch]endlessly repeating error: "poll failed: Bad file descriptor" (Reported by Barry Chern)
* ASTERISK-25202 - Hints extension state broken between 13.3.2 and 13.4 (Reported by cervajs)
* ASTERISK-25196 - res_pjsip_nat: rewrite_contact should not be applied to Contact header when Record-Route headers are present (Reported by Mark Michelson)
* ASTERISK-24907 - res_pjsip_outbound_registration: crash during unload if registration attempts are still occuring (Reported by Kevin Harwell)
* ASTERISK-25204 - res_pjsip_refer: Duplicated Referred-By or Replaces headers on outbound INVITEs. (Reported by Mark Michelson)
* ASTERISK-25171 - Early completion of feature code attended transfer results in intermittent one-way audio, "ghost ringing" and robotic sound. (Reported by Rusty Newton)
* ASTERISK-25189 - AMI: Add Linkedid header to standard channel snapshot information. (Reported by Richard Mudgett)
* ASTERISK-25172 - Crash in channels/sip/sip blind transfer/caller_refer_only test in ast_format_cap_append_from_cap during ast_request (Reported by Matt Jordan)
* ASTERISK-25180 - res_pjsip_mwi: Unsolicited MWI requires reload (Reported by Joshua Colp)
* ASTERISK-25182 - [patch] on CLI sip reload, new codecs get appended only (Reported by Alexander Traud)
* ASTERISK-25163 - Deadlock in chan_sip between reload of sip peer container and MWI Stasis callback (Reported by Dmitriy Serov)
* ASTERISK-25091 - Asterisk REST API - bridge.addChannel crash asterisk when calling channel hangup while adding to bridge (Reported by Ilya Trikoz)
* ASTERISK-24900 - Manager event ParkedCallSwap is not documented (Reported by Rusty Newton)
* ASTERISK-25162 - func_pjsip_aor: Leak of contact in iterator (Reported by Corey Farrell)
* ASTERISK-25158 - res_pjsip: Add option to use AAL2 packing when negotiating g.726 (Reported by Kevin Harwell)
* ASTERISK-24344 - CDR_PROP(disable) disables CDR only for first dialed party (Reported by Janusz Karolak)
* ASTERISK-24443 - CDR fields (dst, dcontext) empty in transfer call started from Macro (Reported by Arveno Santoro)
* ASTERISK-25154 - [patch]fromtag may need to be updated after successful call dialog match (Reported by Damian Ivereigh)
* ASTERISK-25156 - chan_pjsip’s CHAN_START cel event lacks the correct context and exten (Reported by cloos)
* ASTERISK-25157 - bridging: Performing a blonde transfer does not result in connected line updates (Reported by Joshua Colp)
* ASTERISK-25087 - Asterisk segfault when using Directory application with alias option and specific mailbox configuration (Reported by Chet Stevens)
* ASTERISK-24983 - IAX deadlock between hangup and scheduled actions (ex. largrq) (Reported by Y Ateya)
* ASTERISK-25096 - [patch]Segfault when registering over websockets with PJSIP (in ast_sockaddr_isnull at /include/asterisk/netsock2.h) (Reported by Josh Kitchens)
* ASTERISK-24963 - ASAN: heap-use-after-free with PJSIP and WSS (Reported by Badalian Vyacheslav)
* ASTERISK-22559 - gcc 4.6 and higher supports weakref attribute but asterisk doesn't detect it. (Reported by ibercom)
* ASTERISK-25094 - PBX core: Investigate thread safety issues (Reported by Corey Farrell)
* ASTERISK-25148 - res_pjsip NULL channel audit (Reported by Mark Michelson)
* ASTERISK-24717 - ASAN: global-buffer-overflow codec_{ilbc | gsm | adpcm | ipc10} (Reported by Badalian Vyacheslav)
* ASTERISK-25131 - chan_pjsip: In-dialog authentication not handled. (Reported by Richard Mudgett)
* ASTERISK-25100 - asterisk coredump if host has an IPv6 address that end with ::80 (Reported by Mark Petersen)
* ASTERISK-25122 - Large SIP packet received via pjsip over websocket crashes Asterisk (Reported by Ivan Poddubny)
* ASTERISK-25121 - Stasis: Fix unsafe use of stasis_unsubscribe in modules. (Reported by Corey Farrell)
* ASTERISK-24988 - func_talkdetect: Test is bouncing sporadically (Reported by Joshua Colp)
* ASTERISK-25105 - res_pjsip: Possible incompatibility between qualify_timeout and pjproject-2.4 (Reported by George Joseph)
* ASTERISK-25117 - res_mwi_external_ami: Fix manager action registrations. (Reported by Corey Farrell)
* ASTERISK-25112 - Logger: Configuration settings are not reset to default during reload. (Reported by Corey Farrell)
* ASTERISK-24944 - main/audiohook.c change prevents G722 call recording (Reported by Ronald Raikes)
* ASTERISK-24887 - [patch]tags in a=crypto lines do not accept 2 or more digits (Reported by Makoto Dei)
* ASTERISK-25086 - [patch]PJSIP crashes if endpoint missing in Dial() (Reported by snuffy)
* ASTERISK-25089 - res_pjsip_config_wizard: Variable specified in templates aren't being processed correctly (Reported by George Joseph)
* ASTERISK-25090 - CLI core show channel truncates cdr variables (Reported by snuffy)
* ASTERISK-25085 - [patch]Potential crash after unload of func_periodic_hook or test_message (Reported by Corey Farrell)
* ASTERISK-25083 - Message.c: Message channel becomes saturated with frames leading to spammy log messages (Reported by Jonathan Rose)
* ASTERISK-25082 - Asterisk deletes message after doing a playback of an INBOX message using ast_vm_play when the Old folder is full for that mailbox. (Reported by Jonathan Rose)
* ASTERISK-18252 - queue_log mysql time column data format (Reported by Gareth Blades)
* ASTERISK-25041 - [patch]Broken column type checking in res_config_mysql addon (Reported by Alexandre Fournier)
* ASTERISK-21893 - Segfault after call hangup, in ast_channel_hangupcause_set, at channel_internal_api.c (Reported by Aleksandr Gordeev)
* ASTERISK-25074 - Regression: Recent clang-related change broke cross compiling of Asterisk (Reported by Sebastian Kemper)
* ASTERISK-25042 - asterisk.conf options override command-line options. (Reported by Corey Farrell)
* ASTERISK-24442 - Outgoing call files don't work properly when set in the future (Reported by tootai)
* ASTERISK-25057 - res_pjsip_pubsub: Crash in send_notify due to invalid root pointer in sub_tree (Reported by Matt Jordan)
* ASTERISK-24938 - ARI Snoop Channel results in excessive escalating CPU usage (Reported by George Ladoff)
* ASTERISK-25034 - chan_dahdi: Some telco switches occasionally ignore ISDN RESTART requests. (Reported by Richard Mudgett)
* ASTERISK-25003 - Asterisk crashes on attended transfer (using feature) (Reported by Artem Volodin)
* ASTERISK-25038 - Queue log "EXITWITHTIMEOUT" does not always contain waiting time (Reported by Etienne Lessard)
* ASTERISK-25027 - Build System: Many ARI modules are missing dependencies. (Reported by Corey Farrell)
* ASTERISK-25061 - pbx_config: Register manager actions with module version of macro. (Reported by Corey Farrell)
* ASTERISK-25025 - Periodic crashes (in ast_channel_snapshot_create at stasis_channels.c) with Certified Asterisk 13. (Reported by Chet Stevens)
* ASTERISK-25053 - Unit test category /main/presence missing trailing slash. (Reported by Corey Farrell)
* ASTERISK-22708 - res_odbc.conf negative_connection_cache option not respected, failover between DSNs doesn't work (Reported by JoshE)
* ASTERISK-25054 - Formats interface's cannot be unregistered, needs to hold modules until shutdown. (Reported by Corey Farrell)
* ASTERISK-24896 - [patch] Using force black background leads to colours not being reset (Reported by dant)
* ASTERISK-25033 - Asterisk 13 (branch head) won't compile without PJSip (Reported by Peter Whisker)
* ASTERISK-25028 - Build System: Unneeded defines in asterisk/buildopts.h (Reported by Corey Farrell)
* ASTERISK-25048 - Astobj2: Initialization order wrong when both refdebug and AO2_DEBUG are both enabled. (Reported by Corey Farrell)
* ASTERISK-19608 - Asterisk-1.8.x starts rejecting calls with cause code 44 after some time. (Reported by Denis Alberto Martinez)
* ASTERISK-24976 - cdr_odbc not include new columns added on 1.8 (Reported by Rodrigo Ramirez Norambuena)
* ASTERISK-25037 - res_pjsip_outbound_registration: Potential crash in off-nominal failure case when sending message (Reported by Joshua Colp)
* ASTERISK-25022 - Memory leak setting up DTLS/SRTP calls (Reported by Steve Davies)
* ASTERISK-22790 - check_modem_rate() may return incorrect rate for V.27 (Reported by not here)
* ASTERISK-23231 - Since 405693 If we have res_fax.conf file set to minrate=2400, then res_fax refuse to load (Reported by David Brillert)
* ASTERISK-24955 - res_fax: v.27ter support baud rate of 2400, which is disallowed in res_fax's check_modem_rate (Reported by Matt Jordan)
* ASTERISK-24996 - chan_pjsip: Creating Channel Causes Asterisk to Crash When Duplicate AOR Sections Exist in pjsip.conf (Reported by Ashley Sanders)
* ASTERISK-25020 - Mismatched response to outgoing REGISTER request (Reported by Mark Michelson)
* ASTERISK-25018 - pjsip show endpoints crashes asterisk when qualified aors present (Reported by Ivan Poddubny)
* ASTERISK-24749 - ConfBridge: Wrong language on playing conf-hasjoin and conf-hasleft when played to bridge (Reported by Philippe Bolduc)
* ASTERISK-24845 - pjsip send notify not working with Cisco phone (Reported by Carl Fortin)
* ASTERISK-25004 - Crash in authenticated reinvite after originated T.38 FAX (Reported by Mark Michelson)
* ASTERISK-24999 - PJSIP crashes with malformed contact line (Reported by snuffy)
* ASTERISK-24998 - res_corosync: res_corosync tries to load even if res_corosync.conf is missing (Reported by George Joseph)
* ASTERISK-24997 - Astobj2: Some callers of __adjust_lock do not pre-check the object (Reported by Corey Farrell)
* ASTERISK-24982 - res_pjsip_mwi: Unsolicited MWI NOTIFY only sent on mailbox changes (Reported by Joshua Colp)
* ASTERISK-24991 - Check for ao2_alloc failure in __ast_channel_internal_alloc (Reported by Corey Farrell)
* ASTERISK-24895 - After hangup on the side of the ISDN network no HangupRequest event comes for the dahdi channel. (Reported by Andrew Zherdin)
* ASTERISK-24977 - Contacts that don't use qualify are being marked as unavailable (Reported by George Joseph)
* ASTERISK-24774 - Segfault in ast_context_destroy with extensions.ael and extensions.conf (Reported by Corey Farrell)
* ASTERISK-24841 - ConfBridge: Strange sampling rates chosen when channels have multiple native formats (Reported by Matt Jordan)
* ASTERISK-24975 - Enabling 'DEBUG_THREADLOCALS' Causes the Build to Fail (Reported by Ashley Sanders)
* ASTERISK-24863 - res_pjsip: No endpoint events raised via AMI when contacts cannot be reached/qualified (Reported by Dmitriy Serov)
* ASTERISK-24869 - Asterisk segfaults on DAHDI attended transfer due to application (appl) being NULL on unbridged channel (Reported by viniciusfontes)
* ASTERISK-24970 - Crash in res_pjsip_pubsub handling of failed notify (Reported by Scott Griepentrog)
* ASTERISK-13721 - memory leak in "strings.c" (Reported by pj)
* ASTERISK-24959 - [patch]CLI command cdr show pgsql status (Reported by Rodrigo Ramirez Norambuena)
* ASTERISK-24954 - Git migration: Asterisk version numbers are incompatible with the Test Suite (Reported by Matt Jordan)
* ASTERISK-17608 - func_aes.so cannot be loaded if res_crypto / openssl not compiled (Reported by Warren Selby)
* ASTERISK-24928 - [patch]t38_udptl_maxdatagram in pjsip.conf not honored (Reported by Juergen Spies)
* ASTERISK-24835 - Early Media Not working with Chan SIP and Asterisk 13 (Reported by Andrew Nagy)
* ASTERISK-21777 - Asterisk tries to transcode video instead of audio (Reported by Nick Ruggles)
* ASTERISK-24380 - core: Native formats are set to h264 with certain audio/video codec configuration, resulting in path translation WARNINGs (Reported by Matt Jordan)
* ASTERISK-22352 - [patch] IAX2 custom qualify timer is not taken into account (Reported by Frederic Van Espen)
* ASTERISK-24894 - [patch] iax2_poke_noanswer expiration timer too short (Reported by Y Ateya)
* ASTERISK-24935 - res_pjsip_phoneprov_provider: Fix leaked OBJ_MULTIPLE iterator. (Reported by Corey Farrell)
* ASTERISK-23319 - Segmentation fault in queue_exec at app_queue.c (Reported by Vadim)
* ASTERISK-24933 - T38 fails negotiation (Reported by Jonathan Rose)
* ASTERISK-24847 - [security] [patch] tcptls: certificate CN NULL byte prefix bug (Reported by Matt Jordan)
* ASTERISK-21211 - chan_iax2 - unprotected access of iaxs[peer->callno] potentially results in segfault (Reported by Jaco Kroon)
* ASTERISK-18032 - [patch] - IPv6 and IPv4 NAT not working (Reported by Christoph Timm)
* ASTERISK-24910 - "timer=no" and "timer=required" settings in pjsip.conf fail (Reported by Ray Crumrine)
* ASTERISK-24932 - Asterisk 13.x does not build with GCC 5.0 (Reported by Jeffrey C. Ollie)
* ASTERISK-24914 - Division by zero in file.c when playback of voicemail with video as h264 (Reported by Marcello Ceschia)
* ASTERISK-24899 - Parking fall-through behavior different in 13 (Reported by Malcolm Davenport)
* ASTERISK-24937 - [patch]res_pjsip_messaging: Messages may be sent out of order (Reported by Mark Michelson)
* ASTERISK-24920 - Asterisk handles duplicate SIP requests as if they were each a new request (Reported by Mark Michelson)
* ASTERISK-24857 - [patch] "timing test", pjsip incoming/outgoing calls, voicemail prompts and recordings all fail when using the kqueue timer source on FreeBSD 10.x (Reported by Justin T. Gibbs)
* ASTERISK-24155 - [patch]Non-portable and non-reliable recursion detection in ast_malloc (Reported by Timo Teräs)
* ASTERISK-24142 - CCSS: crash during shutdown due to device lookup in destroyed container (Reported by David Brillert)
* ASTERISK-24683 - Crash in PBX ast_hashtab_lookup_internal during core restart now (Reported by Peter Katzmann)
* ASTERISK-24805 - [patch] - ASAN: Race condition (heap-use-after-free) on asterisk closing (Reported by Badalian Vyacheslav)
* ASTERISK-24881 - ast_register_atexit should only be used when absolutely needed (Reported by Corey Farrell)
* ASTERISK-24731 - res_pjsip_session cannot be unloaded (Reported by Corey Farrell)
* ASTERISK-24864 - app_confbridge: file playback blocks dtmf (Reported by Kevin Harwell)
* ASTERISK-14233 - [patch] Buddies are always auto-registered when processing the roster (Reported by Simon Arlott)
* ASTERISK-24780 - [patch] - Buddies are always auto-registered when processing the roster (Reported by Simon Arlott)
* ASTERISK-24781 - PJSIP: Unnecessary 180 Ringing messages sent with undesireabe consequences. (Reported by Richard Mudgett)
* ASTERISK-24879 - [patch]Compilation fails due to 64bit time under OpenBSD (Reported by snuffy)
* ASTERISK-24880 - [patch]Compilation under OpenBSD (Reported by snuffy)
* ASTERISK-21765 - [patch] - FILE function's length argument counts from beginning of file rather than the offset (Reported by John Zhong)
* ASTERISK-24817 - init_logger_chain: unreachable code block (Reported by Corey Farrell)
* ASTERISK-24882 - chan_sip: Improve usage of REF_DEBUG (Reported by Corey Farrell)
* ASTERISK-24876 - Investigate reference leaks from tests/channels/local/local_optimize_away (Reported by Corey Farrell)
* ASTERISK-24840 - res_pjsip: conflicting endpoint identifiers (Reported by Kevin Harwell)
* ASTERISK-16779 - Cannot disallow unknown format '' (Reported by Atis Lezdins)
* ASTERISK-18708 - func_curl hangs channel under load (Reported by Dave Cabot)
* ASTERISK-21038 - Bad command completion of "core set debug channel" (Reported by Richard Kenner)
* ASTERISK-19470 - Documentation on app_amd is incorrect (Reported by Frank DiGennaro)
* ASTERISK-24872 - [patch] AMI PJSIPShowEndpoint closes AMI connection on error (Reported by Dmitriy Serov)
* ASTERISK-23666 - CLONE - nested functions aren't portable (Reported by Diederik de Groot)
* ASTERISK-20399 - Compilation on some systems requires the -fnested-functions flag (Reported by David M. Lee)
* ASTERISK-20850 - [patch]Nested functions aren't portable. Adapting RAII_VAR to use clang/llvm blocks to get the same/similar functionality. (Reported by Diederik de Groot)
* ASTERISK-24807 - Missing mandatory field Max-Forwards (Reported by Anatoli)
* ASTERISK-24808 - res_config_odbc: Improper escaping of backslashes occurs with MySQL (Reported by Javier Acosta)
* ASTERISK-23390 - NewExten Event with application AGI shows up before and after AGI runs (Reported by Benjamin Keith Ford)
* ASTERISK-24786 - [patch] - Asterisk terminates when playing a voicemail stored in LDAP (Reported by Graham Barnett)
* ASTERISK-24739 - [patch] - Out of files -- call fails -- numerous files with inodes from under /usr/share/zoneinfo, mostly posixrules (Reported by Ed Hynan)
* ASTERISK-24755 - Asterisk sends unexpected early BYE to transferrer during attended transfer when using a Stasis bridge (Reported by John Bigelow)
* ASTERISK-24830 - res_rtp_asterisk.c checks USE_PJPROJECT not HAVE_PJPROJECT (Reported by Stefan Engström)
* ASTERISK-24825 - Caller ID not recognized using Centrex/Distinctive dialing (Reported by Richard Mudgett)
* ASTERISK-17588 - Caller ID on TDM410P *UK* PSTN (Reported by Daniel Flounders)
* ASTERISK-24838 - chan_sip: Locking inversion occurs when building a peer causes a peer poke during request handling (Reported by Richard Mudgett)
* ASTERISK-24751 - Integer values in json payload to ARI cause asterisk to crash (Reported by jeffrey putnam)
* ASTERISK-24828 - Fix Frame Leaks (Reported by Kevin Harwell)
* ASTERISK-18105 - most of asterisk modules are unbuildable in cygwin environment (Reported by feyfre)
* ASTERISK-21845 - maxcalls exceeded, Asterisk sends out 480 and also BYE (Reported by Tony Ching)
* ASTERISK-15434 - [patch] When ast_pbx_start failed, both an error response and BYE are sent to the caller (Reported by Makoto Dei)
* ASTERISK-23214 - chan_sip WARNING message 'We are requesting SRTP for audio, but they responded without it' is ambiguous and wrong in some cases (Reported by Rusty Newton)
* ASTERISK-17721 - Incoming SRTP calls that specify a key lifetime fail (Reported by Terry Wilson)
* ASTERISK-20233 - SRTP not working with some devices (Eg Grandstream gxv3175) - Message "Can't provide secure audio requested in SDP offer" (Reported by tootai)
* ASTERISK-22748 - SRTP Crypto Offer With Lifetime Not Accepted (Reported by Alejandro Mejia)
* ASTERISK-24800 - Crash in __sip_reliable_xmit due to invalid thread ID being passed to pthread_kill (Reported by JoshE)
* ASTERISK-24812 - ARI: Creating channels through /channels resource always uses SLIN, which results in unneeded transcoding (Reported by Matt Jordan)
* ASTERISK-24797 - bridge_softmix: G.729 codec license held (Reported by Kevin Harwell)
* ASTERISK-24677 - ARI GET variable on channel provides unhelpful response on non-existent variable (Reported by Joshua Colp)
* ASTERISK-24785 - 'Expires' header missing from 200 OK on REGISTER (Reported by Ross Beer)
* ASTERISK-24499 - Need more explicit debug when PJSIP dialstring is invalid (Reported by Rusty Newton)
* ASTERISK-24724 - 'httpstatus' Web Page Produces Incomplete HTML (Reported by Ashley Sanders)
* ASTERISK-24796 - Codecs and bucket schema's prevent module unload (Reported by Corey Farrell)
* ASTERISK-24814 - asterisk/lock.h: Fix syntax errors for non-gcc OSX with 64 bit integers (Reported by Corey Farrell)
* ASTERISK-24787 - [patch] - Microsoft exchange incompatibility for playing back messages stored in IMAP - play_message: No origtime (Reported by Graham Barnett)
* ASTERISK-22670 - Asterisk crashes when processing ISDN AoC Events (Reported by klaus3000)
* ASTERISK-24689 - Segfault on hangup after outgoing PRI-Euroisdn call (Reported by Marcel Manz)
* ASTERISK-24740 - [patch]Segmentation fault on aoc-e event (Reported by Panos Gkikakis)
* ASTERISK-24799 - [patch] make fails with undefined reference to SSLv3_client_method (Reported by Alexander Traud)
* ASTERISK-24451 - chan_iax2: reference leak in sched_delay_remove (Reported by Corey Farrell)
* ASTERISK-24700 - CRASH: NULL channel is being passed to ast_bridge_transfer_attended() (Reported by Zane Conkle)
* ASTERISK-24791 - Crash in ast_rtcp_write_report (Reported by JoshE)
* ASTERISK-24085 - Documentation - We should remove or further document the 'contact' section in pjsip.conf (Reported by Rusty Newton)
* ASTERISK-24632 - install_prereq script installs pjproject without IPv6 support (Reported by Rusty Newton)
* ASTERISK-24685 - "pjsip show version" CLI command (Reported by Joshua Colp)
* ASTERISK-24768 - res_timing_pthread: file descriptor leak (Reported by Matthias Urlichs)
* ASTERISK-24612 - res_pjsip: No information if a required sorcery wizard is not loaded (Reported by Joshua Colp)
* ASTERISK-24716 - Improve pjsip log messages for presence subscription failure (Reported by Rusty Newton)
* ASTERISK-24771 - ${CHANNEL(pjsip)} - segfault (Reported by Niklas Larsson)
* ASTERISK-24727 - PJSIP: Crash experienced during multi-Asterisk transfer scenario. (Reported by Mark Michelson)
* ASTERISK-24015 - app_transfer fails with PJSIP channels (Reported by Private Name)
* ASTERISK-24741 - dtls_handler causes Asterisk to crash (Reported by Zane Conkle)
* ASTERISK-24701 - Stasis: Write timeout on WebSocket fails to fully disconnect underlying socket, leading to events being dropped with no additional information (Reported by Matt Jordan)
* ASTERISK-24752 - Crash in bridge_manager_service_req when bridge is destroyed by ARI during shutdown (Reported by Richard Mudgett)
* ASTERISK-24772 - ODBC error in realtime sippeers when device unregisters under MariaDB (Reported by Richard Miller)
* ASTERISK-24479 - Enable REF_DEBUG for module references (Reported by Corey Farrell)
* ASTERISK-24742 - [patch] Fix ast_odbc_find_table function in res_odbc (Reported by ibercom)
* ASTERISK-24769 - res_pjsip_sdp_rtp: Local ICE candidates leaked (Reported by Matt Jordan)
* ASTERISK-24748 - res_pjsip: If wizards explicitly configured in sorcery.conf false ERROR messages may occur (Reported by Joshua Colp)
* ASTERISK-24616 - Crash in res_format_attr_h264 due to invalid string copy (Reported by Yura Kocyuba)
* ASTERISK-24737 - When agent not logged in, agent status shows unavailable, queue status shows agent invalid (Reported by Richard Mudgett)
* ASTERISK-24635 - PJSIP outbound PUBLISH crashes when no response is ever received (Reported by Marco Paland)
* ASTERISK-24736 - Memory Leak Fixes (Reported by Mark Michelson)
* ASTERISK-24646 - PJSIP changeset 4899 breaks TLS (Reported by Stephan Eisvogel)
* ASTERISK-24711 - DTLS handshake broken with latest OpenSSL versions (Reported by Jared Biel)
* ASTERISK-24666 - Security Vulnerability: RTP not closed after sip call using unsupported codec (Reported by Y Ateya)
* ASTERISK-24676 - Security Vulnerability: URL request injection in libCURL (CVE-2014-8150) (Reported by Matt Jordan)
* ASTERISK-24729 - Outbound registration not occuring on new registrations after reload. (Reported by Richard Mudgett)
* ASTERISK-24728 - tcptls: Bad file descriptor error when reloading chan_sip (Reported by Kevin Harwell)
* ASTERISK-24715 - chan_sip: stale nonce causes failure (Reported by Kevin Harwell)
* ASTERISK-24485 - res_pjsip cannot be unloaded or shutdown (Reported by Corey Farrell)
* ASTERISK-24719 - ConfBridge recording channels get stuck when recording started/stopped more than once (Reported by Richard Mudgett)
* ASTERISK-24721 - manager: ModuleLoad action incorrectly reports 'module not found' during a Reload operation (Reported by Matt Jordan)
* ASTERISK-24723 - confbridge: CLI command 'confbridge list XXXX' no longer displays user menus (Reported by Matt Jordan)
* ASTERISK-24539 - Compile fails on OSX because of sem_timedwait in bridge_channel.c (Reported by George Joseph)
* ASTERISK-24544 - Compile fails on OSX Yosemite because of incorrect detection of htonll and ntohll (Reported by George Joseph)
* ASTERISK-24231 - crash: CLI execution of realtime destroy sippeers id 1 causes crash due to NULL name provided to ast_variable (Reported by Niklas Larsson)
* ASTERISK-24626 - Voicemail passwords not being stored in ARA (Reported by Paddy Grice)
* ASTERISK-24693 - Investigate and fix memory leaks in Asterisk (Reported by Kevin Harwell)
* ASTERISK-24355 - [patch] chan_sip realtime uses case sensitive column comparison for 'defaultuser' (Reported by HZMI8gkCvPpom0tM)
* ASTERISK-24709 - [patch] msg_create_from_file used by MixMonitor m() option does not queue an MWI event (Reported by Gareth Palmer)
* ASTERISK-24673 - outgoing sip registers cannot be removed or modified without doing restart (or doing module unload chan_sip.so) (Reported by Stefan Engström)
* ASTERISK-24640 - Registration pending stays forever after sip reload (Reported by Max Man)
* ASTERISK-24682 - app_dial: Multiple DialEnd events emitted when MACRO_RESULT or GOSUB_RESULT are an unexpected value (Reported by Matt Jordan)
* ASTERISK-24560 - Creating a named ARI bridge twice causes a crash (Reported by Kinsey Moore)
* ASTERISK-24600 - Stuck IAX channels, Asterisk stops responding to most traffic, potential deadlock (Reported by Jeff Collell)
* ASTERISK-24048 - [patch] contrib/scripts/install_prereq selects 32-bit packages on 64-bit hosts (Reported by Ben Klang)
* ASTERISK-24288 - [patch] - ODBC usage with app_voicemail - voicemail is not deleted after review, hangup (Reported by LEI FU)
* ASTERISK-24615 - When Multiple Transports Exist in pjsip.conf, Incorrect External Addresses is Used in SIP Packets When Responding to INVITE (Reported by David Justl)
* ASTERISK-24624 - Transfer to invalid extension results in hung channel. (Reported by Zane Conkle)
* ASTERISK-24663 - [patch] Unnamed semaphore autoconf check fails on cross compilation (Reported by abelbeck)
* ASTERISK-24655 - res_pjsip_outbound_publish: Hang on shutdown while attempting to publish (Reported by Kevin Harwell)
* ASTERISK-23991 - [patch]asterisk.pc file contains a small error in the CFlags returned (Reported by Diederik de Groot)
* ASTERISK-23850 - Park Application does not respect Return Context Priority (Reported by Andrew Nagy)
* ASTERISK-24665 - Configure check required for pjsip_get_dest_info() (Reported by Mark Michelson)
* ASTERISK-24049 - Asterisk Manager Interface: A number of list type responses aren't using astman_send_listack (Reported by Jonathan Rose)
* ASTERISK-20744 - [patch] Security event logging does not work over syslog (Reported by Michael Keuter)
* ASTERISK-24672 - [PATCH] Memory leak in func_curl CURLOPT (Reported by Kristian Høgh)
* ASTERISK-24474 - sip_to_pjsip.py lacks documentation and does not function (Reported by John Kiniston)
* ASTERISK-24637 - Channel re-enters Stasis() when it should not (Reported by John Bigelow)
* ASTERISK-24591 - Stasis() side of an ARI originated channel cannot be Redirected (Reported by Kinsey Moore)
* ASTERISK-24376 - res_pjsip_refer: REFER request for remote session attempts to direct channel to external_replaces extension instead of context, without providing for the Referred-To SIP URI (Reported by Matt Jordan)
* ASTERISK-24513 - Local channel apparently leaked in off-nominal DTMF attended transfer (Reported by Mark Michelson)
* ASTERISK-24267 - Queue variables associated with setinterfacevar, setqueueentryvar, setqueuevar are not passed to local channel (Reported by Mitch Claborn)
* ASTERISK-23841 - DTMF atxfer doesn't set CallerID for the recall calls to the transferrer. (Reported by Richard Mudgett)
* ASTERISK-24628 - [patch] chan_sip - CANCEL is sent to wrong destination when 'sendrpid=yes' (in proxy environment) (Reported by Karsten Wemheuer)
* ASTERISK-23733 - 'reload acl' fails if acl.conf is not present on startup (Reported by Richard Kenner)
* ASTERISK-24566 - Uninit buf in WS write (Reported by Badalian Vyacheslav)
* ASTERISK-24337 - Spammy DEBUG message needs to be at a higher level - 'Remote address is null, most likely RTP has been stopped' (Reported by Rusty Newton)
* ASTERISK-24459 - bridge_native_rtp: Native RTP bridging is chosen for RTP compatible channels when the DTMF mode is not compatible (Reported by Yaniv Simhi)
* ASTERISK-24536 - AMI redirect with PJSIP fails to move extra channel (Reported by Niklas Larsson)
* ASTERISK-24619 - [patch]Gcc 4.10 fixes in r413589 (1.8) wrongly casts char to unsigned int (Reported by Walter Doekes)
* ASTERISK-24449 - Reinvite for T.38 UDPTL fails if SRTP is enabled (Reported by Andreas Steinmetz)
* ASTERISK-22455 - Asterisk 12 on Ubuntu Lucid deadlocks with DEBUG_THREADS+OPTIONAL_API enabled (Reported by David M. Lee)
* ASTERISK-24614 - Deadlock when DEBUG_THREADS compiler flag enabled (Reported by Richard Mudgett)
* ASTERISK-24604 - res_rtp_asterisk: Crash during restart due to race condition in accessing codec in stored ast_frame and codec core (Reported by Matt Jordan)
* ASTERISK-24563 - Direct Media calls within private network sometimes get one way audio (Reported by Kevin Harwell)
* ASTERISK-24607 - res_pjsip_session: re-INVITE with declined media streams results in 488 (Reported by Matt Jordan)
* ASTERISK-24472 - Asterisk Crash in OpenSSL when calling over WSS from JSSIP (Reported by Badalian Vyacheslav)
* ASTERISK-24514 - res_pjsip_outbound_registration: stack overflow when using non-default sorcery wizard (Reported by Kevin Harwell)
* ASTERISK-24342 - PJSIP: Qualifying endpoints attempts to do them all at the same time. (Reported by Richard Mudgett)
Improvements made in this release:
-----------------------------------
* ASTERISK-26088 - Investigate heavy memory utilization by res_pjsip_pubsub (Reported by Richard Mudgett)
* ASTERISK-25930 - PJSIP: disable multi domain to improve realtime performace (Reported by Alexei Gradinari)
* ASTERISK-25495 - [patch] Prevent old-update packages on repository Debian systems (Reported by Rodrigo Ramirez Norambuena)
* ASTERISK-25846 - Gracefully deal with Absent Stasis Apps (Reported by Andrew Nagy)
* ASTERISK-25791 - res_pjsip_caller_id: Lack of support for Anonymous
* ASTERISK-24813 - asterisk.c: #if statement in listener() confuses code folding editors (Reported by Corey Farrell)
* ASTERISK-25767 - [patch] Add check to configure for sanitizes (Reported by Badalian Vyacheslav)
* ASTERISK-25068 - Move commonly used FreePBX extra sounds to the core set (Reported by Rusty Newton)
* ASTERISK-25627 - Easily Preventable Compile Warning (Reported by Diederik de Groot)
* ASTERISK-25618 - res_pjsip: Check for readability of TLS files at startup (Reported by George Joseph)
* ASTERISK-25572 - Endpoints: Add StatsD stats for Asterisk endpoints (Reported by Matt Jordan)
* ASTERISK-25571 - PJSIP: Add StatsD stats for some common PJSIP objects (Reported by Matt Jordan)
* ASTERISK-25518 - taskprocessor: Add high water mark (Reported by Jonathan Rose)
* ASTERISK-25477 - pjsip show "command" like [criteria] (Reported by Bryant Zimmerman)
* ASTERISK-24718 - [patch]Add inital support of "sanitize" to configure (Reported by Badalian Vyacheslav)
* ASTERISK-24870 - ARI: Subscriptions to bridges generally not super useful (Reported by Matt Jordan)
* ASTERISK-25310 - [patch]on FreeBSD also pthread_attr_init() defaults to PTHREAD_EXPLICIT_SCHED (Reported by Guido Falsi)
* ASTERISK-25256 - [patch]Post AMI VarSet to empty string events when Asterisk deletes a dialplan variable. (Reported by Richard Mudgett)
* ASTERISK-25067 - Sorcery Caching: Implement a new caching module (Reported by Matt Jordan)
* ASTERISK-25040 - pbx: Improve performance of reloads by making hint destruction more performant (Reported by Matt Jordan)
* ASTERISK-25114 - res_pjsip: Add AMI events for chan_pjsip contact lifecycle changes (Reported by George Joseph)
* ASTERISK-25072 - res_pjsip_outbound_registration: line functionality. Additional check for using the request URI (Reported by Dmitriy Serov)
* ASTERISK-25044 - sorcery: Add ability to insert a new wizard into an object type's list (Reported by George Joseph)
* ASTERISK-24892 - Super Awesome Company sound prompts (Reported by Rusty Newton)
* ASTERISK-24744 - Swedish Core Voice prompts (Reported by Tove Hjelm)
* ASTERISK-25043 - [patch] Avoiding ERR_remove_state in OpenSSL (Reported by Alexander Traud)
* ASTERISK-25045 - vector: Add new capabilities and unit tests (Reported by George Joseph)
* ASTERISK-24706 - [patch]add auto-dtmf mode for pjsip (Reported by yaron nahum)
* ASTERISK-25051 - Remove unneeded uses of optional_api providers. (Reported by Corey Farrell)
* ASTERISK-24917 - [patch] clang compilation warnings (Reported by Diederik de Groot)
* ASTERISK-24949 - res_pjsip_outbound_registration: Backport line functionality (Reported by Joshua Colp)
* ASTERISK-24965 - cel_pgsql - log_error string references CDR instead of CEL (Reported by Rodrigo Ramirez Norambuena)
* ASTERISK-24918 - pjsip: add CLI options to display global and system configuration (Reported by Scott Griepentrog)
* ASTERISK-24862 - [patch] Support in-dialog OPTIONS (Reported by yaron nahum)
* ASTERISK-24802 - stasis: set a channel variable on websocket disconnect error (Reported by Kevin Harwell)
* ASTERISK-24133 - [patch]Please support Clang; Allow no-exec stacks (Reported by Jeffrey Walton)
* ASTERISK-24790 - Reduce spurious noise in logs from voicemail - Couldn't find mailbox %s in context (Reported by Graham Barnett)
* ASTERISK-24811 - asterisk-publication sorcery object does not use realtime (Reported by Matt Hoskins)
* ASTERISK-24745 - [patch]Add no_answer to ARI hangup causes (Reported by Ben Merrills)
* ASTERISK-24316 - For httpd server, need option to define server name for security purposes (Reported by Andrew Nagy)
* ASTERISK-24671 - Missing docs for the CDR AMI Event (Reported by Dan Jenkins)
* ASTERISK-24575 - [patch]Make capath work for res_pjsip (Reported by cloos)
* ASTERISK-24678 - [PATCH] Added atxfer * settings to features.conf.sample (Reported by Niklas Larsson)
* ASTERISK-24412 - [patch]Incomplete channel originate/continue handling with ARI (Reported by Nir Simionovich (GreenfieldTech - Israel))
* ASTERISK-24643 - res_pjsip: Add user=phone option (Reported by Matt Jordan)
* ASTERISK-24644 - res_pjsip_keepalive: Add keepalive module for connection-oriented transports. (Reported by Matt Jordan)
* ASTERISK-24553 - ARI/AMI: Include language in standard channel snapshot output (Reported by Matt Jordan)
* ASTERISK-24552 - ARI: Allow associating a channel as an initiator of an Origination for record keeping purposes (Reported by Matt Jordan)
For a full list of changes in this release, please see the ChangeLog:
http://downloads.asterisk.org/pub/telephony/certified-asterisk/ChangeLog-certified-13.8-cert1
Foto di gruppo a fine “Corso Asterisk 13 Avanzato”
Ringraziamo tutti i partecipanti al corso.
Rilasciato Asterisk 13.9.1
Il giorno 13 maggio 2016, il Team di Sviluppo di Asterisk ha annunciato il rilascio di Asterisk Asterisk 13.9.1.
Dal post originale:
The release of Asterisk 13.9.1 resolves an issue reported by the
community and would have not been possible without your participation.
Thank you!
The following is the issue resolved in this release:
Bugs fixed in this release:
-----------------------------------
* ASTERISK-26007 - res_pjsip: Endpoints deleting early after
upgrade from 13.8.2 to 13.9 (Reported by Greg Siemon)
For a full list of changes in this release, please see the ChangeLog:
http://downloads.asterisk.org/pub/telephony/asterisk/ChangeLog-13.9.1
Funzionalità e servizi (non il prezzo) attirano le PMI verso il VoIP
Secondo la recente ricerca di Frost & Sullivan, nei prossimi cinque anni vedremo un importante numero di piccole e medie aziende adottare soluzioni di telefonia cloud-based o centralini hosted. “Le PMI e le start-up di norma sottoscrivono abbonamenti a piattaforme per le Unified Communications interamente cloud-based o hosted, per i benefici e la flessibilità che esse trasferiscono all’utente”, ha affermato l’analista Wonjae Shim. Secondo le valutazioni dei ricercatori, il mercato dei centralini IP hosted per le PMI nella sola america settentrionale raggiungerà i 350 milioni di dollari nei prossimi 5 anni per giungere al picco di un miliardo di dollari entro il 2021, anno in cui il volume totale del mercato in Europa si attesterà a 17.93 miliardi di dollari nel 2021.
Lo studio di Research and Markets indica che gli “early adopters” di servizi di telefonia IP hosted e UCC in Europa sono primariamente le PMI perché hanno tipicamente budget e staff IT più limitati o competenze non sempre sufficienti per installare e gestire in loco soluzioni avanzate per le telecomunicazioni.
Che il prezzo d’acquisto e il costo operativo totale contino è indubbio, ma secondo Frost & Sullivan non sono l’unico driver della scelta di migrare a centralini VoIP hosted. Secondo gli analisti infatti “le PMI desiderano avvalersi di soluzioni di telefonia ‘as a Service’ perché offrono funzionalità avanzate appositamente sviluppate per migliorare le comunicazioni aziendali e l’operatività interna”.
Rilasciato Asterisk 13.9.0
Il giorno 09 maggio 2016, il Team di Sviluppo di Asterisk ha annunciato il rilascio di Asterisk Asterisk 13.9.0.
Dal post originale:
The release of Asterisk 13.9.0 resolves several issues reported by the community and would have not been possible without your participation.
Thank you!
The following are the issues resolved in this release:
Bugs fixed in this release:
-----------------------------------
* ASTERISK-25963 - func_odbc requires reconnect checks for stale connections (Reported by Ross Beer)
* ASTERISK-25970 - Segfault in pjsip_url_compare (Reported by Dmitriy Serov)
* ASTERISK-25938 - res_odbc: MySQL/MariaDB statement LAST_INSERT_ID() always returns zero. (Reported by Edwin Vandamme)
* ASTERISK-25927 - Removed option "registertrying" is still documented in sip.conf.sample (Reported by Etienne Lessard)
* ASTERISK-25947 - Protocol transfers to stasis applications are missing the StasisStart with the replace_channel object. (Reported by Richard Mudgett)
* ASTERISK-24649 - Pushing of channel into bridge fails; Stasis fails to get app name (Reported by John Bigelow)
* ASTERISK-24782 - StasisEnd event not present for channel that was swapped out for another after completing attended transfer (Reported by John Bigelow)
* ASTERISK-25942 - res_pjsip_caller_id: Transfer results in mixed ConnectedLine information (Reported by George Joseph)
* ASTERISK-25928 - res_pjsip: URI validation done outside of PJSIP thread (Reported by Joshua Colp)
* ASTERISK-25929 - res_pjsip_registrar: AOR_CONTACT_ADDED events not raised (Reported by Joshua Colp)
* ASTERISK-25934 - chan_sip should not require sipregs or updateable sippeers table unless rt (Reported by Jaco Kroon)
* ASTERISK-25888 - Frequent segfaults in function can_ring_entry() of app_queue.c (Reported by Sébastien Couture)
* ASTERISK-25796 - res_pjsip: DOS/Crash when TCP/TLS sockets exceed pjproject PJ_IOQUEUE_MAX_HANDLES (Reported by George Joseph)
* ASTERISK-25707 - Long contact URIs or hostnames can crash pjproject/Asterisk under certain conditions (Reported by George Joseph)
* ASTERISK-25123 - Bracketed IPv6 Contact header parameter unparsable with Asterisk/PJSIP (Reported by Anthony Messina)
* ASTERISK-25874 - app_voicemail: Stack buffer overflow in test_voicemail_notify_endl (Reported by Badalian Vyacheslav)
* ASTERISK-25912 - chan_local passes AST_CONTROL_PVT_CAUSE_CODE without adding them to the local hangupcauses via ast_channel_hangupcause_hash_set (Reported by Jaco Kroon)
* ASTERISK-25885 - res_pjsip: Race condition between adding contact and automatic expiration (Reported by Joshua Colp)
* ASTERISK-25910 - pjproject: Via headers are not parsed when "received" contains an IPv6 address (Reported by George Joseph)
* ASTERISK-25890 - Asterisk 13.8.0 alembic database update fails (Reported by Harley Peters)
* ASTERISK-25894 - [patch] webrtc video broken due to missing marker bits in RTP streams (Reported by Jacek Konieczny)
* ASTERISK-25854 - No audio after HOLD/RESUME - incorrect a=recvonly in SDP from Asterisk (Reported by Robert McGilvray)
* ASTERISK-25873 - res_pjsip: Bundled pjproject: compile error, cannot find -lasteriskpj (Reported by Hans van Eijsden)
* ASTERISK-25882 - ARI: Crash can occur due to race condition when attempting to operate on a hung up channel (Part 2) (Reported by Richard Mudgett)
* ASTERISK-25867 - [patch] Video delay on app_echo (Reported by Jacek Konieczny)
* ASTERISK-24605 - res_parking option parkeddynamic does not work with the core Features 'parkcall' (DTMF initiated parking) (Reported by Philip Correia)
* ASTERISK-25826 - PJSIP / Sorcery slow load from realtime (Reported by Ross Beer)
* ASTERISK-24596 - Unclear how to use Park application with res_parking 'parkeddynamic' enabled. Documentation? (Reported by Philip Correia)
* ASTERISK-24543 - Asterisk 13 responds to SIP Invite with all possible codecs configured for peer as opposed to intersection of configured codecs and offered codecs (Reported by Taylor Hawkes)
* ASTERISK-25825 - Crashes during shutdown when running CLI commands (Reported by Mark Michelson)
* ASTERISK-25407 - Asterisk fails to log to multiple syslog destinations (Reported by Elazar Broad)
* ASTERISK-25510 - [patch]Log to syslog failing (Reported by Michael Newton)
* ASTERISK-25857 - func_aes: incorrect use of strlen() leads to data corruption (Reported by Gianluca Merlo)
Improvements made in this release:
-----------------------------------
* ASTERISK-25865 - Message-Account Missing From PJSIP MWI (Reported by Ross Beer)
* ASTERISK-25444 - [patch]Music On Hold Warning misleading (Reported by Conrad de Wet)
For a full list of changes in this release, please see the ChangeLog:
http://downloads.asterisk.org/pub/telephony/asterisk/ChangeLog-13.9.0